Cybersecurity Capacity Maturity Model for Nations
Cybersecurity Capacity Maturity Model for Nations (CMM) is a framework developed to review the cybersecurity capacity maturity of a country across five dimensions.[1] The five dimensions covers the capacity area required by a country to improve its cybersecurity posture.[2] It was designed by Global Cyber Security Capacity Centre (GCSCC) of University of Oxford and first of its kind framework for countries to review their cybersecurity capacity, benchmark it and receive recommendation for improvement.[3] Each dimension is divided into factors and the factors broken down into aspects.[2] The review process includes rating each factor or aspect along five stages that represents the how well a country is doing in respect to that factor or aspect.[2] The recommendations includes guidance on areas of cybersecurity that needs improvement and thus will require more focus and investment.[3] As at June, 2021, the framework has been adopted and implemented in over 80 countries worldwide.[4] Its deployment has been catalyzed by the involvement of international organizations such as the Organization of American States (OAS), the World Bank (WB), the International Telecommunication Union (ITU) and the Commonwealth Telecommunications Union (CTO) and Global Forum on Cyber Expertise (GFCE).[5]
Overview
The World Summit on Information Society identified capacity building in the realm of cybersecurity as one of the pillars necessary to reap the benefits of processes and services digitalization, especially in developing nations.[6] The International Telecommunication Union reported that developing nations lack the necessary cybersecurity capacity to manage ICT risk and respond to cyberthreats.[7] Because cyberattacks and vulnerabilities in one nation can affect other parts of the world, some maturity models were developed to assess the cybersecurity capacity of nations and benchmark the capacity level.[8] One of such models is the CMM.[8]
The CMM was developed in 2014, through collaborative effort between the GCSCC and over 200 experts from academia, international and regional organizations and the private sector.[9] CMM assesses the capacity of a country from five identified area called dimensions with the objective of improving the coverage, measurement and effectiveness of cyber security capacity building within five levels of progression.[10] Benchmarking of a country's cybersecurity capacity involves reviewing its initiatives and activities against the entire CMM and across all Dimensions.[2] According to the report of a regional CMM assessment of Latin America and the Caribbean, CMM assessment aims to identify cybersecurity gaps and discover actions that works.[11]
Since 2014, the CMM has undergone revisions and it is intended to be a living model that remain relevant to every aspect of cybersecurity needs at the national level.[2]
Structure
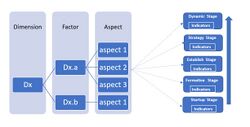
The framework consists of dimensions, factors, aspects, indicators and stages.[2]
Dimension.
The dimensions represent the scope of a country's cybersecurity capacity that will be assessed by CMM and it is broken down into factors.[2] The dimensions are not stand alone, rather they are related to one another because a nation's performance in one dimension of capacity may require input from another dimension.[2]
The five dimensions from the 2021 version are:[2]
- Developing cybersecurity policy and strategy - This dimension examines how a nation fares in terms of availability and implementation of Cybersecurity policies and strategy.
- Encouraging responsible cybersecurity culture within society - This dimension views how well citizens of a nation are familiar with digital risk and the provision of a viable channel for reporting cybercriminal activities.
- Building cybersecurity knowledge and capabilities - This dimension explores structures in place for cybersecurity awareness and education within the nation.
- Creating effective legal and regulatory frameworks - Examine the ability of a country to develop, ratify and enforce cybersecurity and privacy related legislation.
- Controlling risks through standards and technologies - This dimension examines the common use of cybersecurity standard and presence of structures for development of such technologies.
Factors:
The factors are the important component of a country's capacity whose maturity level is measured and there are 23 factors in the latest version with each having one
or more aspects [2]
Aspects:
These are smaller subdivision of factors which helps with understanding each factor and help in evidence gathering and measurement.[2]
Indicators:
Each Indicator define the actions that suggest that a nation has maintain a specific stage of maturity.[2] The level of maturity assigned to an aspect depend on the ability of a nation to fulfill the steps and actions listed as its indicator.[3] Evidence will be required to be provided before a particular stage can be attained.[3] It is either an
evidence is available or not and to move to a higher stage, all of the Indicators within a particular stage will need to have been fulfilled.[2]
Stage:
This represent how matured a nations is on each factor or aspect.[2] There are 5 stages of maturity; start-up, formative, established, strategic and dynamic. For a nation to met a particular maturity stage, it has to fulfill some indicators.[3]
- Start-up - At this stage, a nation has no presentable evidence to show existence of cybersecurity initiatives.
- Formative - Evidence is available to proof initiatives on some of the aspects, however these efforts may be at the initiation state or be ad hoc.
- Established - The is evidence to show that the aspect is defined, functional and working but adequate resource allocation is lacking.
- Strategic - Aspect has been prioritized based on national need.
- Dynamic - A working adaptable cybersecurity strategy is available, which is evidenced by global leadership on cybersecurity issues, agility of decision-making, and resources allocation.
Development
The first version of the framework was released in 2014.[12] Based on pilot assessments conducted in six countries, improvements were made on the model and an updated version was published in 2017. Based on lessons learnt over the years from CMM deployments and consultations from GCSCC Expert Advisory Panel, strategic, regional and implementation partners of the GCSCC, and other experts from academia, international and regional organisations, governments, the private sector, and civil society, an updated version was released in 2021.[13]
The dimensions, factors and aspects have changed overtime between CMM versions. The 2014 has 5 dimensions and 21 factors.[12] The 2017 version has 5 dimensions with 24 factors.[11] The 2021 version has 5 dimensions and 23 factors.[2]
Table 1 lists the dimensions across the three versions.
| Dimensions | 2014/2017 | 2021 |
|---|---|---|
| D1 | Cybersecurity Policy and Strategy | Developing cybersecurity policy and strategy |
| D2 | Cyber Culture and Society | Encouraging responsible cybersecurity culture within society |
| D3 | Cybersecurity Education, Training and Skills | Building cybersecurity knowledge and capabilities |
| D4 | Legal and Regulatory Frameworks | Creating effective legal and regulatory frameworks |
| D5 | Standards, organisations, and technologies | Controlling risks through standards and technologies |
Table 2 list the factors for each version.
| Factors | 2014 | 2017 | 2021 |
|---|---|---|---|
| D1.1 | Documented or Official National Cybersecurity Strategy | National Cybersecurity Strategy | National Cybersecurity Strategy |
| D1.2 | Incident Response | Incident Response | Incident Report and Crisis Management |
| D1.3 | Critical National Infrastructure | Critical Infrastructure (CI) Protection | Critical Infrastructure (CI) Protection |
| D1.4 | Crisis Management | Crisis Management | Cybersecurity in Defense and National Security |
| D1.5 | Cyber Defence Consideration | Cyber Defence consideration | |
| D1.6 | Digital Redundancy | Communications redundancy | |
| D2.1 | Cybersecurity Mind-set | Cybersecurity mind-set | Cybersecurity Mindset |
| D2.2 | Cybersecurity Awareness | Trust and confidence on the Internet | Trust and Confidence in Online Service |
| D2.3 | Confidence and Trust on the Internet | User understanding of personal information protection on the Internet | User Understanding of Personal Information Protection Online |
| D2.4 | Privacy Online | Reporting mechanisms | Reporting Mechanisms |
| D2.5 | Media and social media | Media and Social Media | |
| D3.1 | National Availability of Cyber Education and Training | Raising awareness | Building Cybersecurity Awareness |
| D3.2 | National Development of Cyber Security Education | Framework for education | Cybersecurity Education |
| D3.3 | Training and Educational Initiatives within the Public and Private Sector | Framework for professional training | Cybersecurity Professional Training |
| D3.4 | Corporate Governance, Knowledge and Standards | Cybersecurity Research and Innovation | |
| D4.1 | Cybersecurity Legal Frameworks | Legal frameworks | Legal and Regulatory Provisions |
| D4.2 | Legal Investigation | Criminal justice system | Related Legislative Framework |
| D4.3 | Responsible Reporting | Formal and informal cooperation frameworks to combat cybercrime | Legal and Regulatory capability and Capacity |
| D4.4 | Formal and Informal Co-operation Frameworks to Combat Cybercrime | ||
| D5.1 | Adherence to Standards | Adherence to standards | Adherence to Standards |
| D5.2 | Cybersecurity Coordinating Organisations | Internet infrastructure resilience | Security Controls |
| D5.3 | National Infrastructure Resilience | Software quality | Software Quality |
| D5.4 | Cybersecurity Marketplace | Technical security controls | Communications and Internet Infrastructure Resilience |
| D5.5 | Cryptographic controls | Cybersecurity Marketplace | |
| D5.6 | Cybersecurity marketplace | Responsible Disclosure | |
| D5.7 | Responsible disclosure |
The Review Process
CMM review process has 3 stages.[3][14]
Stage 1: Desk research and country-partner identification.
The first step is selection of a country. A CMM review can be requested by a country or a country can be selected for assessment by an international or regional organization.[3]
Once a nation is selected for assessment, a relationship is established with the host country and necessary stakeholders identified from academia, civil societies, government ministries/department, international organizations and the private sector.[2]
Stage 2: The Review
The actual review with the stakeholders is a three-day consultation process and based on the five dimensions, multiple teams are created across stakeholders .[2]
Open discussions or focus groups method is applied to ask and answers questions.[3] Questions and answer can also be collected using online tool.[15] Inability to provide evidence for all indicators under each aspect will result in a lower maturity level for that aspect.[3]
Remote follow-up sessions or email communication may be used for further data collection.[3]
Stage 3: Review Report
A report is presented to the country's government and it is at the discretion of that country to make it publicly available or not.[2]
The recommendation
The output of the CMM assessment is a report which details the gaps identified from each aspect and the present maturity level of each indicator.[15] The assessment report is the property of the assessed nation [16] and they choose whether to make it public or not.[3] Depending on a nation's need, it recommend areas that should be given priority in terms of resource allocation.[2]
The report include a sunburst representation of the cybersecurity capacity of the nation, reason for placing each factor or aspect in a particular stage and recommendation of what can be done to move up along the maturity stage.[17]
Sample results from some of the reviews are available on GCSCC's website.[4]
Nations with CMM Assessment
The GCSCC website has the list of nations that has been assessed, which have been listed below.[4]
Albania
Antigua and Barbuda
Argentina
Armenia
Bahamas
Bangladesh
Barbados
Belize
Benin
Bhutan
Bolivia
Bosnia and Herzegovina
Botswana
Brazil
Burkina Faso
Cabo Verde
Cameroon
Chile
Colombia
Cook Islands
Costa Rica
Cyprus
Dominica
Dominican Republic
Ecuador
El Salvador
Eswatini
Fiji
Gambia
Georgia
Ghana
Grenada
Guatemala
Guyana
Haiti
Honduras
Iceland
Indonesia
Ivory Coast
Jamaica
Kiribati
Kosovo
Kyrgyzstan
Lesotho
Liberia
Lithuania
Madagascar
Malawi
Mauritius
Mexico
Micronesia
Montenegro
Morocco
Mozambique
Myanmar
Namibia
Nicaragua
Niger
Nigeria
North Macedonia
Panama
Papua New Guinea
Paraguay
Peru
Rwanda
Saint Kitts and Nevis
Saint Lucia
Saint Vincent and the Grenadines
Samoa
Senegal
Serbia
Sierra Leone
Somalia
Sri Lanka
Suriname
Switzerland
Tanzania
Thailand
Tonga
Trinidad and Tobago
Tunisia
Tuvalu
Uganda
United Kingdom
Uruguay
Vanuatu
Venezuela
Zambia
References
- ↑ "Global Cyber Security Capacity Centre | Digital Watch". https://dig.watch/actors/global-cyber-security-capacity-centre.
- ↑ 2.00 2.01 2.02 2.03 2.04 2.05 2.06 2.07 2.08 2.09 2.10 2.11 2.12 2.13 2.14 2.15 2.16 2.17 2.18 Global Cyber Security Capacity Centre (2021). "Cybersecurity Capacity Maturity Model for Nations (CMM)". https://cybilportal.org/wp-content/uploads/2021/03/CMM2021-Edition-March-2021.pdf.
- ↑ 3.00 3.01 3.02 3.03 3.04 3.05 3.06 3.07 3.08 3.09 3.10 The World Bank. "Global Cybersecurity Capacity Program. "Lessons Learned and Recommendations towards strengthening the Program"". https://documents1.worldbank.org/curated/en/947551561459590661/pdf/Global-Cybersecurity-Capacity-Program-Lessons-Learned-and-Recommendations-towards-Strengthening-the-Program.pdf.
- ↑ 4.0 4.1 4.2 "CMM Reviews around the World" (in en). https://gcscc.ox.ac.uk/cmm-reviews#/.
- ↑ RAND (2017). "Developing Cybersecurity Capacity. A proof-of-concept implementation guide". https://www.rand.org/content/dam/rand/pubs/research_reports/RR2000/RR2072/RAND_RR2072.pdf.
- ↑ International Telecommunication Union (2015). "WSIS+10 Statement on the Implementation of the WSIS Outcomes". https://www.itu.int/net/wsis/review/inc/docs/final/wsis10.statement.pdf.
- ↑ "Enhancing Cybersecurity in Least Developed Countries" (in en-US). https://www.itu.int:443/en/ITU-D/Cybersecurity/Pages/CYBLDC.aspx.
- ↑ 8.0 8.1 "Advancing Cybersecurity Capacity Building: Implementing a Principle-Based Approach" (in en-US). https://www.gppi.net/2017/03/06/advancing-cybersecurity-capacity-building-implementing-a-principle-based-approach.
- ↑ "National cybersecurity capacity maturity assessment". https://www.nrdcs.lt/en/services/national-cybersecurity-capacity-maturity-assessment-/28.
- ↑ Klimburg, Alexander; Zylberberg, Hugo (2015). "Cyber Security Capacity Building: Developing Access". https://www.files.ethz.ch/isn/195765/NUPI_Report_6_15.pdf.
- ↑ 11.0 11.1 "2020 Cybersecurity Report: Risks, Progress, and the Way Forward in Latin America and the Caribbean | Publications". https://publications.iadb.org/publications/english/document/2020-Cybersecurity-Report-Risks-Progress-and-the-Way-Forward-in-Latin-America-and-the-Caribbean.pdf.
- ↑ 12.0 12.1 Global Cyber Security Capacity Centre (2015). "Cybersecurity Capacity Assessment of the Republic of Kosovo". https://gcscc.ox.ac.uk/files/cmmreviewreportkosovojune2015pdf.
- ↑ "Development and Evolution of the CMM" (in en). https://gcscc.ox.ac.uk/development-and-evolution-of-the-cmm#/.
- ↑ "CMM Review Process" (in en). https://gcscc.ox.ac.uk/cmm-review-process#/.
- ↑ 15.0 15.1 Organization of American States (2016). "Cybersecurity Are We Ready in Latin America and the Caribbean?". https://gcscc.ox.ac.uk/files/cybersecurity-are-we-prepared-latin-america-and-caribbeanpdf.
- ↑ Designer (2019-11-22). "The CMM - Oceania Cyber Security Centre" (in en-AU). https://ocsc.com.au/capacity-initiatives/the-cmm/.
- ↑ The World Bank (April 2019). "CYBERSECURITY CAPACITY REVIEW The Gambia". https://www.pura.gm/wp-content/uploads/2019/07/CMM-report_Gambia_2019.pdf.
 |
