Network enclave
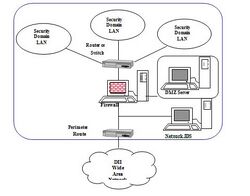
A network enclave is a section of an internal network that is subdivided from the rest of the network.[1][2]
Purpose
The purpose of a network enclave is to limit internal access to a portion of a network. It is necessary when the set of resources differs from those of the general network surroundings.[3][4] Typically, network enclaves are not publicly accessible. Internal accessibility is restricted through the use of internal firewalls, VLANs, network admissions control and VPNs.[5]
Scenarios
Network Enclaves consist of standalone assets that do not interact with other information systems or networks. A major difference between a DMZ or demilitarized zone and a network enclave is a DMZ allows inbound and outbound traffic access, where firewall boundaries are traversed. In an enclave, firewall boundaries are not traversed. Enclave protection tools can be used to provide protection within specific security domains. These mechanisms are installed as part of an Intranet to connect networks that have similar security requirements.[6]
DMZ within an enclave
A DMZ can be established within an enclave to host publicly accessible systems. The ideal design is to build the DMZ on a separate network interface of the enclave perimeter firewall. All DMZ traffic would be routed through the firewall for processing and the DMZ would still be kept separate from the rest of the protected network.
References
- ↑ Northcutt, Stephen. "Protected Enclaves Defense-in-Depth". http://www.sans.edu/research/security-laboratory/article/372. Retrieved 2015-10-08.
- ↑ "Term:Enclave - FISMApedia". http://fismapedia.org/index.php/Term:Enclave. Retrieved 2015-10-08.
- ↑ "Network Enclaves – Enhanced Internal Network Segmentation | Where Trust is Key!". 2009-08-13. Archived from the original on 2013-02-13. https://web.archive.org/web/20130213181752/http://trustcc.wordpress.com/2009/08/13/network-enclaves-%E2%80%93-enhanced-internal-network-segmentation/. Retrieved 2015-10-08.
- ↑ Rome, James. "Enclaves and Collaborative Domains web.oml.gov". http://web.ornl.gov/~webworks/cppr/y2001/pres/117259.pdf.
- ↑ "Protected Enclaves Defense-in-Depth". http://www.sans.edu/research/security-laboratory/article/372. Retrieved 2015-10-08.
- ↑ "THE ROLE OF FIREWALLS AND GUARDS IN ENCLAVE BOUNDARY PROTECTION". https://www.hsdl.org/?view&did=18524.
 |
