Organization:milw0rm
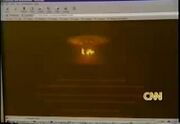 Milw0rm on CNN | |
| Formation | 1998 |
|---|---|
Membership | JF, Keystroke, ExtreemUK, savec0re, and VeNoMouS |
Milw0rm is a group of hacktivists[1] best known for penetrating the computers of the Bhabha Atomic Research Centre (BARC) in Mumbai , the primary nuclear research facility of India , on June 3, 1998.[2] The group conducted hacks for political reasons,[3] including the largest mass hack up to that time, inserting an anti-nuclear weapons agenda and peace message on its hacked websites.[4][5] The group's logo featured the slogan "Putting the power back in the hands of the people."[6]
The BARC attack generated heated debate on the security of information in a world prevalent with countries developing nuclear weapons and the information necessary to do so, the ethics of "hacker activists" or "hacktivists," and the importance of advanced security measures in a modern world filled with people willing and able to break into insecure international websites.
The exploit site milw0rm.com and str0ke are unaffiliated with the milw0rm hacker group.
Members
Little is known about the members of milw0rm, which is typical of hacking groups, which often conceal members' identities to avoid prosecution.[7] The international hacking team "united only by the Internet"[citation needed][8] was composed of teenagers[9] who went by the aliases of JF, Keystroke, ExtreemUK, savec0re, and VeNoMouS.[10] VeNoMouS, 18, hailed from New Zealand, ExtreemUK and JF, 18, from England, Keystroke, 16, from the US and Savec0re, 17, from the Netherlands.
JF went on to achieve a modicum of notoriety when MTV "hacked" its own website intentionally and graffitied the words "JF Was Here" across the page,[11] at the same time that JF was under investigation for the milw0rm attacks by Scotland Yard.[12] Hundreds of pages hosted on MTV.com sported the new JF logo, including one page that read, "JF was here, greets to milw0rm".[13] MTV later confirmed that the alleged JF "hack" was a publicity stunt to promote the appearance of a commentator named Johnny Fame at the 1998 MTV Video Music Awards.[12] Many were puzzled by the apparent hack committed by JF since the hacker was "known for relatively high ethical standards."[12]
VeNoMouS claimed that he learned to crack into systems from Ehud Tenenbaum, an Israeli hacker known as The Analyzer.[14]
BARC attack
Four days before the incident, the five permanent members of the United Nations Security Council, the US, Russia , United Kingdom , France and China , denounced both India and Pakistan for unilaterally declaring themselves nuclear weapons states. The day before the attack, Jacques Gansler, US Undersecretary of Defense for acquisition and technology, warned a military conference that teenage hackers posed "a real threat" to national security.
On the night of June 3, 1998, from their workstations on three continents, the group used a US military .mil machine[14] to break into the LAN, or local area network, of BARC and gained root access. The center's website, connected to the LAN, and their firewall were not secured enough to prevent the group from entering and gaining access to confidential emails and documents. The emails included correspondence between the center's scientists relating to their development of nuclear weapons and analysis of five recent nuclear tests.[citation needed] Milw0rm took control of six servers and then posted a statement of anti-nuclear intentions on the center's website.[citation needed]
In the process of the break-in, the multinational group of teenagers – from the United States , United Kingdom and New Zealand – gained access to five megabytes of classified documents pertaining to India's nuclear weapons program.[15] Savec0re erased all the data on two servers as a protest against the center's nuclear capabilities. To display their security breach publicly, they changed the center's webpage to display a mushroom cloud along with an anti-nuclear message and the phrase "Don't think destruction is cool, coz its not".[16]
Milw0rm then came forward with the security flaws they exploited in BARC's system, along with some of the thousands of pages of documents they had lifted from the server, concerning India's last five nuclear detonations.
The group's purpose for the attack was to protest nuclear testing, according to Savec0re, VeNoMouS and JF, in their correspondence with Wired's reporter James Glave.[16]
After the attack Keystroke claimed that the breach had taken "13 minutes and 56 seconds" to execute. Many news organizations reported breathlessly how the teenagers had penetrated a nuclear research facility in "less than 14 minutes." However, examining more closely the hacker's wording and tone in the interview, and especially the specificity of the "56 seconds" claim, it is apparent that Keystroke meant this as a lighthearted answer to the question, "Exactly how long did it take you?". The actual invasion took careful planning, routing through servers throughout the world from three different continents, and took days to execute. An Indian news agency reported that downloading thousands of pages from India's slow servers would have taken much longer than 14 minutes.[17]
Attack aftermath
The security breach was first reported by Wired News. JF and VeNoMouS claimed credit [citation needed] by emailing Wired reporter James Glave with documents they had obtained from the BARC servers as proof.[16]
After first denying that any incident had occurred, BARC officials admitted that the center had indeed been hacked and emails had been downloaded. An official at BARC downplayed the severity and importance of the incident,[17] announcing that the security flaw resulted from "a very normal loophole in Sendmail," while going on to state that the center had not bothered to download a new version of the Sendmail program, responsible for the center's email servers. The center also admitted that after milw0rm's breach, the site had been hacked into again, this time with less severe consequences. Forbes wrote that perhaps up to 100 hackers had followed milw0rm's footsteps into the BARC servers once they were revealed as insecure.[18] The website was shut down while its security was upgraded. Later, a senior US government official told ZDNet that the Indians had known about the flaw and had chosen to ignore it, creating the opportunity for milw0rm to root the servers.[16] BARC officials said that none of the emails contained confidential information, the group did not destroy data, and that the computers they have that contain important data were isolated from the ones broken into.[17]
Nevertheless, the breach was a severe one and had the potential to cause an incident of international proportions. Forbes called it "potentially the most devastating" hacking incident of 1998.[18] After the attack, members of the group participated in an anonymous Internet Relay Chat (IRC) chat with John Vranesivich, the founder of hacking news website Anti-Online. Keystroke claimed how if he wanted to, he could have sent threatening emails from the Indian email server to a Pakistani email server. He also claimed that if the group had possessed malicious intentions, the consequences for both south Asian countries could have been catastrophic.
For these reasons, the milw0rm attack caused other groups to heighten their security to prevent invasion by hackers. The U.S. Army announced, without giving evidence as to why they believed this to be the case, that the hacks might have originated in Turkey, noting that "Turkey is the primary conduit for cyber attacks." A senior US official said that the CIA had obtained the material that milw0rm had purloined and was reviewing it—the official did not mention how the CIA obtained this information.[16]
Later, Wired revealed that an Indian national and self-proclaimed terrorist, Khalid Ibrahim, had approached members of milw0rm and other hacker groups on IRC—including Masters of Downloading and the Noid—and attempted to buy classified documents from them. According to savec0re, Ibrahim threatened to kill him if the hacker did not turn over the classified documents in question.[19] Savec0re told Kevin Mitnick that Ibrahim first approached him posing as a family member of an FBI agent who could grant immunity to the members of milw0rm.[20]
The Electronic Disturbance Theater released a statement in support of JF, applauding him for his hacktivism and maintaining that computer break-ins of this sort were not cyber-terrorism as some claim.[21]
The event received wide international coverage, with reports by CNN, MSNBC and the Associated Press in the days following.[22]
Other attacks
One month after the BARC incident, in July 1998, milw0rm hacked the British web hosting company Easyspace, putting their anti-nuclear mushroom cloud message on more than 300 of Easyspace's websites,[23] along with text that read: "This mass takeover goes out to all the people out there who want to see peace in this world."[24]
Wired reported that this incident was perhaps the "largest 'mass hack' ever undertaken."[24] The United States Department of Defense adviser John Arquilla later wrote that it was one of the largest hacks ever seen.[25] Some of the sites hacked in the incident were for the World Cup, Wimbledon, the Ritz Casino, Drew Barrymore, and the Saudi royal family.[24] The text placed on the sites read in part, "This mass takeover goes out to all the people out there who want to see peace in this world... This tension is not good, it scares you as much as it scares us. For you all know that this could seriously escalate into a big conflict between India and Pakistan and possibly even World War III, and this CANNOT happen...[24] Use your power to keep the world in a state of PEACE."[26]
While scanning a network for weaknesses, members of the group came across EasySpace, a British company which hosted many sites on one server. Along with members of the fellow hacking group Ashtray Lumberjacks,[6] milw0rm had the revised mushroom cloud image and text on all of Easyspace's websites in less than one hour.[24] Vranesevich said that the mass hack was rare in its effect and its intention: the hackers seemed to be more interested in political purposes than exposing computer security flaws.[24]
It was also reported that milw0rm broke into a Turkish nuclear facility in addition to BARC.[27]
See also
References
- ↑ "'Hacktivists' of All Persuasions Take Their Struggle to the Web". New York Times. October 31, 1998. http://www.pixelyze.com/scrapbook/articles/nyt103198/31hack.html.
- ↑ Milworm Bites BARC outlookindia.com. Retrieved 30 December 2012
- ↑ Margolis, Michael; David Resnick (2000). Politics As Usual. Sage Publications. p. 195. ISBN 0-7619-1330-0.
- ↑ Wall, David; William L. Simon (2001). Crime and the Internet. London: Routledge. p. 65. ISBN 0-415-24429-3. https://archive.org/details/crimeinternet00wall.
- ↑ Himma, Kenneth Einar (2006). Internet security. Jones & Bartlett Publishers. pp. 64–65. ISBN 0-7637-3536-1.
- ↑ 6.0 6.1 "E-Guerrillas in the mist". Ottawa Citizen. October 27, 1998. http://hrea.org/lists/huridocs-tech/markup/msg00014.html.
- ↑ Himma, Kenneth Einar (2006). Internet security. Jones & Bartlett Publishers. p. 92. ISBN 0-7637-3536-1.
- ↑ Smallridge, Joshua (2016). "Understanding Cyber-Vigilantism: A Conceptual Framework". Journal of Theoretical & Philosophical Criminology 8: 57–70. ProQuest 1787752058. https://www.proquest.com/docview/1787752058.
- ↑ Rashtriya Sahara. India: Sahara India Mass Communication. 1996.
- ↑ Boni, William C.; Gerald L. Kovacich (1999). I-way robbery. Butterworth-Heinemann. p. 142. ISBN 0-7506-7029-0.
- ↑ "MTV "hack" backfires". CNet. September 9, 1998. http://news.cnet.com/2100-1023-215319.html.
- ↑ 12.0 12.1 12.2 "MTV Cries 'Hacked!'". Wired. September 9, 1998. https://www.wired.com/culture/lifestyle/news/1998/09/14914.
- ↑ "AntiOnline's Editorial Coverage Of The MTV Site "Hack" ?". AntiOnline. September 1998. http://antionline.com/SpecialReports/mtv/opinion.html.
- ↑ 14.0 14.1 "Crackers: We Stole Nuke Data". Wired. June 3, 1998. https://www.wired.com/science/discoveries/news/1998/06/12717.
- ↑ Liang, Qiao; Al Santoli (2002). Unrestricted warfare. NewsMax Media. p. 35. ISBN 0-9716807-2-8. https://archive.org/details/isbn_9780971680722/page/35.
- ↑ 16.0 16.1 16.2 16.3 16.4 "India has scary nuke hack". ZDNet. June 5, 1998. http://news.zdnet.com/2100-9595_22-510664.html.
- ↑ 17.0 17.1 17.2 "The Eye of the Needle". Rediff. June 9, 1998. http://www.rediff.com/computer/1998/jun/09barc.htm.
- ↑ 18.0 18.1 "Hacking Bhabha". Forbes. November 16, 1998. https://www.forbes.com/1998/11/16/feat.html.
- ↑ "Do Terrorists Troll the Net?". Wired. November 4, 1998. https://www.wired.com/politics/law/news/1998/11/15812.
- ↑ Mitnick, Kevin; William L. Simon (2005). The Art of Intrusion. John Wiley and Sons. p. 33. ISBN 0-7645-6959-7. https://archive.org/details/artintrusionreal00mitn_335.
- ↑ "The Electronic Disturbance Theater supports "JF" the young british anti-nuclear hacker". The Electronic Disturbance Theater. July 8, 1998. http://www.thing.net/~rdom/ecd/Brithacker.html.
- ↑ "In the News". AntiOnline. http://www.antionline.com/about.php?action=inthenews.
- ↑ Boni, William C.; Gerald L. Kovacich (1999). I-way robbery. Butterworth-Heinemann. p. 130. ISBN 0-7506-7029-0.
- ↑ 24.0 24.1 24.2 24.3 24.4 24.5 "Anti-Nuke Cracker Strikes Again". Wired. July 3, 1998. http://www.thing.net/~rdom/ecd/Brithacker.html.
- ↑ Arquilla, John; David F. Ronfeldt (2001). Networks and netwars. Rand Corporation. p. 273. ISBN 0-8330-3030-2. https://archive.org/details/networksnetwars00john/page/273.
- ↑ "Cyberwarriors: Activists and Terrorists Turn to Cyberspace". The Future of War. Summer 2001. http://hir.harvard.edu/articles/print.php?article=905.
- ↑ Defensor Pacis. The Institute. 1999.
External links
Mirrors of hacked sites
 |
