Path protection
| Communication protocol | |
| Purpose | To protect against inevitable failures on service providers’ network that might affect the services offered to end customers |
|---|---|
| RFC(s) | 3031 |
Path protection in telecommunications is an end-to-end protection scheme used in connection oriented circuits in different network architectures to protect against inevitable failures on service providers’ network that might affect the services offered to end customers. Any failure occurred at any point along the path of a circuit will cause the end nodes to move/pick the traffic to/from a new route. Finding paths with protection, especially in elastic optical networks, was considered a difficult problem, but an efficient and optimal algorithm was proposed.[1]
Other techniques to protect telecommunications networks against failures are: Channel Protection, Link Protection, Segment-Protection, and P-cycle Protection
Path protection in ring-based networks
In ring-based networks topology where the setup is to form a closed loop among the Add Drop Multiplexers, there is basically one path related ring protection scheme available in Unidirectional Path-Switched Ring[2] architecture. In SDH networks, the equivalent of UPSR is Sub-Network Connection Protection (SNCP). Note that SNCP does not assume a ring topology, and can also be used in mesh topologies.
In UPSR, the data is transmitted in both directions, clock and counter clock wise, at the source ADM. At the destination then, both signals are compared and the best one of the two is selected. If a failure occurs then the destination just needs to switch to the unaffected path.
Path protection in optical mesh network
Circuits in optical mesh networks can be unprotected, protected to a single failure, and protected to multiple failures. The end optical switches in protected circuits are in charge of detecting the failure, in some cases requesting digital cross connects or optical cross-connects in intermediate devices, and switching the traffic to/from the backup path. When the primary and backup paths are calculated, it is important that they are at least link diverse so that a single link failure does not affect both of them at the same time. They can also be node diverse, which offers more protection in case a node failure occurs; depending on the network sometimes the primary and backup path cannot be provisioned to be node diverse at the edges, ingress and egress, node.
There are two types of path protection in Optical Mesh Networks:[3] Dedicated Backup Path Protection and Shared Backup Path Protection
Dedicated backup path protection or DBPP (1+1)
In DBPP, both the primary and backup path carry the traffic end to end, then it is up to the receiver to decide which of the two incoming traffic it is going to pick; this is exactly the same concept as in Ring Based Path Protection. Since the optics along both paths are already active, DBPP is the fastest protection scheme available, usually in the order of a few tens of milliseconds, because there is no signaling involved in between ingress and egress nodes thus only needing the egress node to detect the failure and switch the traffic over to the unaffected path. Being the fastest protection scheme also makes it the most expensive; normally using more than double of the provisioned capacity for the primary because the backup path is usually longer due to the link and/or node diversity rule of thumb.[4]
Shared backup path protection or SBPP
The concept behind this protection scheme is to share a backup channel among different, link/node diverse, primary paths. In other words, one backup channel can be used to protect various primary paths as shown on the figure below where the link between S and T is used to protect both AB and CD primaries. Under normal operations, assuming no failure on the network, the traffic is carried on the primary paths only; the shared backup path is only used when there is a failure in one of those primary paths.[5]
There are two approaches to provision or reserve backups channels. First, there is the failure dependent assignment or approach also known as restoration in which the backup path is calculated in real time after the failure occurs. This technique is found in early versions of Mesh networks. However, in today’s Optical Mesh Network it can be used as a re-provisioning technique to help recover a second failure when the backup resources are already in use. The down side to restoration as a protection technique is that the recovery time is not fast enough.[5]
The second approach is to have a predefined backup path computed before the failure. This approach is said to be failure independent and it takes less processing time to recover as compared to the failure dependent approach. Here the backup path is calculated together with the primary at provisioning time. Even though the backup path is calculated, it is not assigned to a specific circuit before a failure occurs; cross connect requests are initiated after the fact on a first-come, first-served basis. Since this approach can only protect from a single failure at a time, if a second primary path fails and at least a portion of its backup path is already in used, this path won't be able to recover unless restoration technique is in place for such cases.[5]
There is a general down side to both of the above approaches and is that assuming there is a link failure with several paths running through it, each path in that link is going to be recovered individually. This implies that the total time the last path on that link is going to take to be back in service through the secondary path will be the sum of all other previous recovery times plus its own. This could affect the committed SLA (Service Level Agreement) to the customer.[5]
Path protection in MPLS networks
Multi-Protocol Label Switching (MPLS)[6][7] architecture is described in the RFC-3031. It is a packet-based network technology that provides a framework for recovery through the creation of point to point paths called Label Switched Paths (LSP). These LSPs creation are between a head-end and a tail-end label switch router (LSR). In the former case, the head-end router is the input or ingress router. In the latter case the tail-end represents the output or egress router in the path. There are a few protection techniques for MPLS[8] very similar in the general concept to those for Optical Mesh Networks, such as link protection (e.g., MPLS local protection) and path protection. The path protection schemes for MPLS are as follow:
Packet protection scheme (1+1)
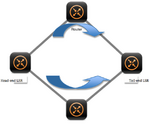
This protection scheme is similar in a sense to Ring-based path protection and Dedicated Backup Path Protection (DBPP) schemes described before. Here, same traffic is transmitted over two, link and/or node disjoint, LSPs; primary and backup. The transmission is done by the head-end LSR. The tail-end LSR then receives and compares both traffics; when a failure occurs, the tail-end detects it and switches the traffic to the secondary LSP. As with DBPP in Optical Mesh Network, there is no signaling involved in this protection scheme. This technique is the simplest and fastest of all, but as it reserves and transmits packets on both LSP, it takes away bandwidth that could be shared and used by other LSPs.
Global path protection (1:1)

In this protection scheme, a primary and a backup LSP are computed and setup at the provisioning time prior to failures. The backup LSP does not necessarily need to have the same constrain in terms of bandwidth as the primary; it is possible to reserve less bandwidth on the backup LSP and not incur in packet loss when in use. This is because the bandwidth of the link is shared among the different LSPs and the reason why the previous explained protection scheme is not preferred. It is also true that the Backup LSP does not necessarily carry traffic unless the primary LSP fails. When this occurs, a fault indication signal (FIS) is sent back to the head-end LSR that will immediately switch the traffic to the backup LSP. The drawback in this protection scheme is that the longer the LSPs, the longer the recovery time will be because of the travel time of the FIS notification.
See also
- SONET
- Add-drop Multiplexer (ADM)
- Optical Mesh Networks
- Shortest Path Problem
- K Shortest Path Routing
- Link Protection
- Segment Protection
- Shared Risk Resource Group
- MPLS
- Service Level Agreement
References
- ↑ Ireneusz Szcześniak; Ireneusz Olszewski; Bożena Woźna-Szcześniak (2021). "Towards an Efficient and Exact Algorithm for Dynamic Dedicated Path Protection". Entropy 23 (9): 1116. doi:10.3390/e23091116. PMID 34573741. Bibcode: 2021Entrp..23.1116S.
- ↑ Unidirectional Path Switched Ring (UPSR).
- ↑ Eric Bouillet; Georgios Ellinas; Jean-Francois Labourdette; Ramu Ramamurthy (2007). Path Routing in Mesh Optical Networks. John Wiley & Sons, Ltd. ISBN 978-0-470-01565-0.
- ↑ Eric Bouillet; Georgios Ellinas; Jean-Francois Labourdette; Ramu Ramamurthy (2007). Path Routing in Mesh Optical Networks. John Wiley & Sons, Ltd. pp. 31, 43, 84. ISBN 978-0-470-01565-0.
- ↑ 5.0 5.1 5.2 5.3 Eric Bouillet; Georgios Ellinas; Jean-Francois Labourdette; Ramu Ramamurthy (2007). Path Routing in Mesh Optical Networks. John Wiley & Sons, Ltd. pp. 32, 44, 86. ISBN 978-0-470-01565-0.
- ↑ Jean Philippe Vasseur, Mario Pickavet & Piet Demeester (2004). Network Recovery, Protection and Restoration of Optical, SONET-SDH, IP, and MPLS. Morgan Kaufmann Publishers. ISBN 0-12-715051-X.
- ↑ Bruce S. Davie; Adrian Farrel (2008). MPLS: Next Steps. Morgan Kaufmann Publishers. ISBN 978-0-12-374400-5.
- ↑ V. Sharma; F. Hellstrand (February 2003). RFC 3469: Framework for Multi-Protocol Label Switching (MPLS)-based Recovery. IETF. doi:10.17487/RFC3469. http://tools.ietf.org/html/rfc3469.
Further reading
- An Overview of DWDM Networks
- "Path Routing in Mesh Optical Networks", by Eric Bouillet, Georgios Ellinas, Jean-Francois Labourdette, and Ramu Ramamurthy [1], [2], [3]
- "Network Recovery: Protection and Restoration of Optical, SONET-SDH, IP, and MPLS", by Jean-Philippe Vasseur, Mario Pickavet, and Piet Demeester, 2004 [4]
- "Gmpls Technologies: Broadband Backbone Networks and Systems" by Naoaki Yamanaka, Kohei Shiomoto, and EIJI AUTOR OKI [5]
- Jean-Philippe Vasseur, Mario Pickavet, and Piet Demeester. Network Recovery, Protection and Restoration of Optical, SONET-SDH, IP, and MPLS. Morgan Kaufmann Publishers, 2004.
- Addressing Transparency in DWDM mesh survivable networks by Sid Chaudhuri, Eric Bouillet, and Georgios Ellinas[yes|permanent dead link|dead link}}]
- Shared Path Protection in DWDM Mesh Networks
- The Multiple Path Protection of DWDM Backbone Optical Networks
- RFC-3031
- G.841
 |
