Private set intersection
| General | |
|---|---|
| Related to | homomorphic encryption |
Private set intersection is a secure multiparty computation cryptographic technique[1] that allows two parties holding sets to compare encrypted versions of these sets in order to compute the intersection. In this scenario, neither party reveals anything to the counterparty except for the elements in the intersection.
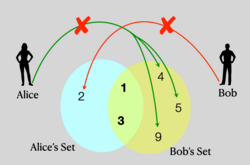
Other variants of this exist, such as the server-client scenario, in which only the client learns the intersection of her set with the set of the server, without the server learning intersection of his set with the clients. [2]
For the comparison of data sets by cryptographic hashes on a small or predictable domain, precautions should be taken to prevent dictionary attacks.[3]
Apple uses this technique in Password Monitoring.[4] It has proposed using the technology for its announced Expanded Protections for Children [5]
In general, PSI protocols can be categorized into two broad categories: (1) traditional PSI and (2) delegated PSI. In the traditional PSI category, the data owners interact directly with each other and need to have a copy of their set at the time of the computation, e.g.,.[6] In the delegated PSI the computation of PSI and/or the storage of sets can be delegated to a third-party server (that is itself might be a passive or active adversary). The delegated PSI category can be further divided into two classes: (a) those that support one-off delegation, and (b) those that support repeated delegation. The PSI protocols that support one-off delegation require the data owner to re-encode its data and send the encoded data to the server for each computation, e.g.,.[7] Those that support repeated delegation allow the data owners to upload their (encrypted) data to the server only once, and then re-use it many times for each computation carried out but the server, e.g.,[8]
Recently, researchers have proposed a variant of PSI protocol (in both traditional and delegated categories) that support data update, e.g., .[9][10] This type of PSI protocol lets data owners insert/delete set elements into/from their data with low overheads and in a privacy-preserving manner.
Educational example
This educational example demonstrated the key idea of PSI, but does not provide real-world cryptographic security (hence should not be used with real-world data).
# Example sets
party_a_set = {'apple', 'banana', 'cherry'}
party_b_set = {'banana', 'orange', 'apple'}
# Hashing the elements in both sets
hashed_party_a_set = {hash(e) for e in party_a_set}
hashed_party_b_set = {hash(e) for e in party_b_set}
# Finding the intersection of the hashed sets
intersection = hashed_party_a_set.intersection(hashed_party_b_set)
# Printing hashed intersection for demonstration
print(intersection)
References
- ↑ Chen, Hao; Laine, Kim; Rindal, Peter (2018-05-16) (in en-US). Fast Private Set Intersection from Homomorphic Encryption. Association for Computing Machinery. ISBN 9781450349468. https://www.microsoft.com/en-us/research/publication/fast-private-set-intersection-homomorphic-encryption/.
- ↑ Pinkas, Benny (in en-US). Private Set Intersection. https://cyber.biu.ac.il/wp-content/uploads/2017/01/15.pdf.

- ↑ Ihle, Cornelius; Schubotz, Moritz; Meuschke, Norman; Gipp, Bela (2020-08-02). "A First Step Towards Content Protecting Plagiarism Detection" (in en). Proceedings of the ACM/IEEE Joint Conference on Digital Libraries in 2020. Virtual Event China: ACM. pp. 341–344. doi:10.1145/3383583.3398620. ISBN 978-1-4503-7585-6.

- ↑ "Password Monitoring". https://support.apple.com/guide/security/password-monitoring-sec78e79fc3b/. Retrieved 8 August 2021.
- ↑ "Child Safety". https://www.apple.com/child-safety/. Retrieved 8 August 2021.
- ↑ Freedman, Michael J; Nissim, Kobbi; Pinkas, Benny (2004). "Efficient private matching and set intersection". International Conference on the Theory and Applications of Cryptographic Techniques'04: Proceedings. Lecture Notes in Computer Science 3027: 1–19. doi:10.1007/978-3-540-24676-3_1. ISBN 978-3-540-21935-4. https://link.springer.com/chapter/10.1007/978-3-540-24676-3_1.pdf.
- ↑ Kamara, Seny; Mohassel, Payman; Raykova, Mariana; Sadeghian, Saeed (2014). "Scaling private set intersection to billion-element sets". International Conference on Financial Cryptography and Data Security'14: Proceedings: 195–215. https://fc14.ifca.ai/papers/fc14_submission_52.pdf.
- ↑ Abadi, Aydin; Terzis, Sotirios; Dong, Changyu (2016). "VD-PSI: verifiable delegated private set intersection on outsourced private datasets". International Conference on Financial Cryptography and Data Security'16: Proceedings: 149–168. https://fc14.ifca.ai/papers/fc14_submission_52.pdf.
- ↑ Abadi, Aydin; Dong, Changyu; Murdoch, Steven J; Terzis, Sotirios (2022). "Multi-party Updatable Delegated Private Set Intersection". International Conference on Financial Cryptography and Data Security'22: Proceedings. https://fc22.ifca.ai/preproceedings/68.pdf.
- ↑ Badrinarayanan, Saikrishna; Miao, Peihan; Xie, Tiancheng (2022). "Updatable Private Set Intersection". Privacy Enhancing Technologies'22:Proceedings 2022 (2): 378–406. doi:10.2478/popets-2022-0051. https://petsymposium.org/2022/files/papers/issue2/popets-2022-0051.pdf.
 |
