Screened subnet
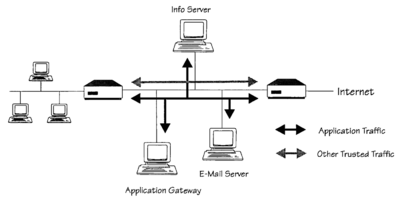
In network security a screened subnet refers to the use of one or more logical screening routers as a firewall to define three separate subnets: an external router (sometimes called an access router), that separates the external network from a perimeter network, and an internal router (sometimes called a choke router) that separates the perimeter network from the internal network. The perimeter network, also called a border network or demilitarized zone (DMZ), is intended for hosting servers (sometimes called bastion hosts) that are accessible from or have access to both the internal and external networks.[1][2][3] The purpose of a screened subnet or DMZ is to establish a network with heightened security that is situated between an external and presumed hostile network, such as the Internet or an extranet, and an internal network.
A screened subnet is an essential concept for e-commerce or any entity that has a presence in the World Wide Web or is using electronic payment systems or other network services because of the prevalence of hackers, advanced persistent threats, computer worms, botnets, and other threats to networked information systems.
Physical separation of routers
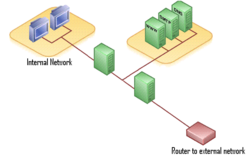
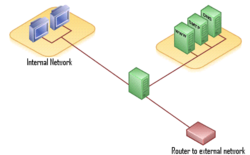
By separating the firewall system into two separate component routers it achieves greater potential throughput by reducing the computational load of each router. As each component router of the screened subnet firewall needs to implement only one general task, each router has a less complex configuration. A screened subnet or DMZ can also be achieved by a single firewall device with three network interfaces.[4]
Relationship to DMZ
The term demilitarized zone in military context refers to an area in which treaties or agreements between contending groups forbid military installations and activities, often along an established frontier or boundary between two or more military powers or alliances. The similarity to network security is that the screened network (DMZ) has reduced fortifications because it has intended points of ingress from the external network which is presumed to be hostile.
It appears that the term demilitarized zone (DMZ) was popularized as a sales and marketing term sometime after the development of screened routers and firewalls. It is often used as a synonym but may have once had a different meaning.
- "There are a number of terms that are used, such as bastion hosts, screened subnets, DMZ, or perimeter networks that can be confusing, especially when used together." ... "Another term that may often causes confusion is the DMZ (demilitarized zone), as opposed to a screened subnet. A true DMZ is a network that contains hosts accessible from the internet with only the exterior, or boarder, router between them. These hosts are not protected by a screening router." ... "A screened subnet may also be a collection of hosts on a subnet, but these are located behind a screening router. The term DMZ may be used by a vendor to mean either, so it is best to verify which they mean."[5]
Comparison to screened host firewall / architecture
Whereas the screened subnet firewall employs two screened routers to create three subnets, a screened host firewall employs only one screened router to define two subnets: an external network and an internal network.[6][7][8] The screened subnet firewall is more secure because an intruder must traverse two filtered routes to reach the internal network. If the bastion / DMZ host is compromised the intruder must still bypass the second filtered route to reach internal network hosts.
See also
- DMZ (computing)
- Firewall (networking)
- Multitier architecture
References
- ↑ Wack, John; Carnahan, Lisa (December 1994). "3.4 Screened Subnet Firewall". Keeping Your Site Comfortably Secure: An Introduction to Internet Firewalls. National Institute of Standards and Technology. pp. 38–40. doi:10.6028/NIST.SP.800-10. https://csrc.nist.gov/publications/detail/sp/800-10/archive/1994-12-01.
- ↑ Chapman, D. Brent; Zwicky, Elizabeth D. (November 1995). "6.3. Screened Subnet Architectures". Building Internet Firewalls (1st ed.). O'Reilly & Associates. ISBN 1-56592-124-0. https://docstore.mik.ua/orelly/networking_2ndEd/fire/ch06_03.htm.
- ↑ "ISACA CISA Study Exam". ISACA. 2018. https://icisa2018.exam-study.com/QuestionSession.aspx?q=69&id=18ee8e2f-1b16-46e0-8270-d4828d4cd1b6. Retrieved 16 October 2018. "A screened-subnet firewall, also used as a demilitarized zone (DMZ), utilizes two packet filtering routers and a bastion host. This provides the most secure firewall system because it supports both network- and application-level security while defining a separate DMZ network."
- ↑ Jacobs, Stuart (2015). Engineering Information Security: The Application of Systems Engineering Concepts to Achieve Information Assurance. John Wiley & Sons. pp. 563. ISBN 9781119101604. https://books.google.com/books?id=2eQ2yxTA3tUC&dq=dual+firewall+dmz&pg=PA296.
- ↑ Davis, William S. (September 20, 2000). "Use offense to inform defense. Find flaws before the bad guys do.". SANS Institute. https://cyber-defense.sans.org/resources/papers/gsec/firewalls-started-100289.
- ↑ Wack, John; Carnahan, Lisa (December 1994). "3.3 Screened Host Firewall". Keeping Your Site Comfortably Secure: An Introduction to Internet Firewalls. National Institute of Standards and Technology. pp. 36–38. doi:10.6028/NIST.SP.800-10. https://csrc.nist.gov/publications/detail/sp/800-10/archive/1994-12-01.
- ↑ Chapman, D. Brent; Zwicky, Elizabeth D. (November 1995). "6.2. Screened Host Architectures". Building Internet Firewalls (1st ed.). O'Reilly & Associates. ISBN 1-56592-124-0. https://docstore.mik.ua/orelly/networking_2ndEd/fire/ch06_02.htm.
- ↑ "ISACA CISA Study Exam". ISACA. 2018. https://icisa2018.exam-study.com/QuestionSession.aspx?q=69&id=18ee8e2f-1b16-46e0-8270-d4828d4cd1b6. Retrieved 16 October 2018. "A screened-host firewall utilizes a packet filtering router and a bastion host. This approach implements basic network layer security (packet filtering) and application server security (proxy services)."
 |
