Triangular network coding
In coding theory, triangular network coding (TNC) is a non-linear network coding based packet coding scheme introduced by (Qureshi Foh).[1] Previously, packet coding for network coding was done using linear network coding (LNC). The drawback of LNC over large finite field is that it resulted in high encoding and decoding computational complexity. While linear encoding and decoding over GF(2) alleviates the concern of high computational complexity, coding over GF(2) comes at the tradeoff cost of degrading throughput performance.
The main contribution of triangular network coding is to reduce the worst-case decoding computational complexity of to (where n is the total number of data packets being encoded in a coded packet) without degrading the throughput performance, with code rate comparable to that of optimal coding schemes.
Triangular code has also been proposed as Fountain code[2] to achieve near-optimal performance with encoding and decoding computational complexity of . It has been further shown that triangular based fountain code can even outperform optimized Luby transform code.[2]
Coding and decoding
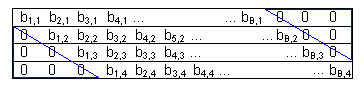
In TNC, coding is performed in two stages. First redundant "0" bits are added at the head and tail of each packet such that all packets are of uniform bit length. Then the packets are XOR coded, bit-by-bit. The "0" bits are added in such a way that these redundant "0" bits added to each packet generate a triangular pattern.
In essence, the TNC decoding process, like the LNC decoding process involves Gaussian elimination. However, since the packets in TNC have been coded in such a manner that the resulting coded packets are in triangular pattern, the computational process of triangularization,[3] with complexity of , where is the number of packets, can be bypassed. The receiver now only needs to perform back-substitution,[3] with worst-case complexity given as for each bit location.
References
- ↑ Qureshi, Jalaluddin; Foh, Chuan Heng; Cai, Jianfei (2012). "Optimal solution for the index coding problem using network coding over GF(2)". 2012 9th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON). pp. 134–142. doi:10.1109/SECON.2012.6275780. ISBN 978-1-4673-1905-8. Bibcode: 2012arXiv1209.6539Q..
- ↑ 2.0 2.1 Qureshi, Jalaluddin (August 2023). "Triangular code: Near-optimal linear time fountain code". Digital Communications and Networks 9 (4): 869-878. doi:10.1016/j.dcan.2022.12.006. https://www.sciencedirect.com/science/article/pii/S2352864822002747.
- ↑ 3.0 3.1 J. B. Fraleigh, and R. A. Beauregard, Linear Algebra. Chapter 10, Addison-Wesley Publishing Company, 1995.
 |
