Disaster recovery
Disaster recovery is the process of maintaining or reestablishing vital infrastructure and systems following a natural or human-induced disaster, such as a storm or battle. It employs policies, tools, and procedures. Disaster recovery focuses on information technology (IT) or technology systems supporting critical business functions[1] as opposed to business continuity. This involves keeping all essential aspects of a business functioning despite significant disruptive events; it can therefore be considered a subset of business continuity.[2][3] Disaster recovery assumes that the primary site is not immediately recoverable and restores data and services to a secondary site.
IT service continuity
IT Service Continuity[4][5] (ITSC) is a subset of business continuity planning (BCP)[6] that focuses on Recovery Point Objective (RPO) and Recovery Time Objective (RTO). It encompasses IT disaster recovery planning and wider IT resilience planning. It also incorporates IT infrastructure and services related to communications, such as telephony and data communications.
Principles of backup sites
Planning includes arranging for backup sites, whether they are "hot" (operating prior to a disaster), "warm" (ready to begin operating), or "cold" (requires substantial work to begin operating), and standby sites with hardware as needed for continuity.
In 2008, the British Standards Institution launched a specific standard supporting Business Continuity Standard BS 25999, titled BS25777, specifically to align computer continuity with business continuity. This was withdrawn following the publication in March 2011 of ISO/IEC 27031, "Security techniques — Guidelines for information and communication technology readiness for business continuity."[7]
ITIL has defined some of these terms.[8]
Recovery Time Objective
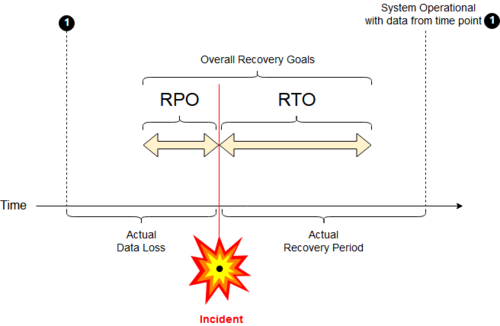
The Recovery Time Objective (RTO)[9][10] is the targeted duration of time and a service level within which a business process must be restored after a disruption in order to avoid a break in business continuity.[11]
According to business continuity planning methodology, the RTO is established during the Business Impact Analysis (BIA) by the owner(s) of the process, including identifying time frames for alternate or manual workarounds.
RTO is a complement of RPO. The limits of acceptable or "tolerable" ITSC performance are measured by RTO and RPO in terms of time lost from normal business process functioning and data lost or not backed up during that period.[11][12]
Recovery Time Actual
Recovery Time Actual (RTA) is the critical metric for business continuity and disaster recovery.[9]
The business continuity group conducts timed rehearsals (or actuals), during which RTA gets determined and refined as needed.[9][13]
Recovery Point Objective
A Recovery Point Objective (RPO) is the maximum acceptable interval during which transactional data is lost from an IT service.[11]
For example, if RPO is measured in minutes, then in practice, off-site mirrored backups must be continuously maintained as a daily off-site backup will not suffice.[14]
Relationship to Recovery Time Objective
A recovery that is not instantaneous restores transactional data over some interval without incurring significant risks or losses.[11]
RPO measures the maximum time in which recent data might have been permanently lost and not a direct measure of loss quantity. For instance, if the BC plan is to restore up to the last available backup, then the RPO is the interval between such backups.
RPO is not determined by the existing backup regime. Instead business impact analysis determines RPO for each service. When off-site data is required, the period during which data might be lost may start when backups are prepared, not when the backups are secured off-site.[12]
Data synchronization points
A data synchronization point[15] is a backup is completed. It halts update processing while a disk-to-disk copy is completed. The backup[16] copy reflects the earlier version of the copy operation; not when the data is copied to tape or transmitted elsewhere.
System design
RTO and the RPO must be balanced, taking business risk into account, along with other system design criteria.[17]
RPO is tied to the times backups are secured offsite. Sending synchronous copies to an offsite mirror allows for most unforeseen events. The use of physical transportation for tapes (or other transportable media) is common. Recovery can be activated at a predetermined site. Shared offsite space and hardware complete the package.[18]
For high volumes of high-value transaction data, hardware can be split across multiple sites.
History
Planning for disaster recovery and information technology (IT) developed in the mid to late 1970s as computer center managers began to recognize the dependence of their organizations on their computer systems.
At that time, most systems were batch-oriented mainframes. An offsite mainframe could be loaded from backup tapes pending recovery of the primary site; downtime was relatively less critical.
The disaster recovery industry[19][20] developed to provide backup computer centers. Sungard Availability Services was one of the earliest such centers, located in Sri Lanka (1978).[21][22]
During the 1980s and 90s, computing grew exponentially, including internal corporate timesharing, online data entry and real-time processing. Availability of IT systems became more important.
Regulatory agencies became involved; availability objectives of 2, 3, 4 or 5 nines (99.999%) were often mandated, and high-availability solutions for hot-site facilities were sought.[citation needed]
IT service continuity became essential as part of Business Continuity Management (BCM) and Information Security Management (ICM) as specified in ISO/IEC 27001 and ISO 22301 respectively.
The rise of cloud computing since 2010 created new opportunities for system resiliency. Service providers absorbed the responsibility for maintaining high service levels, including availability and reliability. They offered highly resilient network designs. Recovery as a Service (RaaS) is widely availability and promoted by the Cloud Security Alliance.[23]
Classification
Disasters can be the result of three broad categories of threats and hazards.
- Natural hazards include acts of nature such as floods, hurricanes, tornadoes, earthquakes, and epidemics.
- Technological hazards include accidents or the failures of systems and structures such as pipeline explosions, transportation accidents, utility disruptions, dam failures, and accidental hazardous material releases.
- Human-caused threats that include intentional acts such as active assailant attacks, chemical or biological attacks, cyber attacks against data or infrastructure, sabotage, and war.
Preparedness measures for all categories and types of disasters fall into the five mission areas of prevention, protection, mitigation, response, and recovery.[24]
Planning
Research supports the idea that implementing a more holistic pre-disaster planning approach is more cost-effective. Every $1 spent on hazard mitigation (such as a disaster recovery plan) saves society $4 in response and recovery costs.[25]
2015 disaster recovery statistics suggest that downtime lasting for one hour can cost[26]
- small companies $8,000,
- mid-size organizations $74,000, and
- large enterprises $700,000 or more.
As IT systems have become increasingly critical to the smooth operation of a company, and arguably the economy as a whole, the importance of ensuring the continued operation of those systems, and their rapid recovery, has increased.[27]
Control measures
Control measures are steps or mechanisms that can reduce or eliminate threats. The choice of mechanisms is reflected in a disaster recovery plan (DRP).
Control measures can be classified as controls aimed at preventing an event from occurring, controls aimed at detecting or discovering unwanted events, and controls aimed at correcting or restoring the system after a disaster or an event.
These controls are documented and exercised regularly using so-called "DR tests".
Strategies
The disaster recovery strategy derives from the business continuity plan.[28] Metrics for business processes are then mapped to systems and infrastructure.[29] A cost-benefit analysis highlights which disaster recovery measures are appropriate. Different strategies make sense based on the cost of downtime compared to the cost of implementing a particular strategy.
Common strategies include:
- backups to tape and sent off-site
- backups to disk on-site (copied to off-site disk) or off-site
- replication off-site, such that once the systems are restored or synchronized, possibly via storage area network technology
- private cloud solutions that replicate metadata (VMs, templates and disks) into the private cloud. Metadata are configured as an XML representation called Open Virtualization Format, and can be easily restored
- hybrid cloud solutions that replicate both on-site and to off-site data centers. This provides instant fail-over to on-site hardware or to cloud data centers.
- high availability systems which keep both the data and system replicated off-site, enabling continuous access to systems and data, even after a disaster (often associated with cloud storage).[30]
Precautionary strategies may include:
- local mirrors of systems and/or data and use of disk protection technology such as RAID
- surge protectors — to minimize the effect of power surges on delicate electronic equipment
- use of an uninterruptible power supply (UPS) and/or backup generator to keep systems going in the event of a power failure
- fire prevention/mitigation systems such as alarms and fire extinguishers
- anti-virus software and other security measures.
Disaster recovery as a service
Disaster recovery as a service (DRaaS) is an arrangement with a third party vendor to perform some or all DR functions for scenarios such as power outages, equipment failures, cyber attacks, and natural disasters.[31]
See also
References
- ↑ Systems and Operations Continuity: Disaster Recovery. Georgetown University. University Information Services. Retrieved 3 August 2012.
- ↑ Disaster Recovery and Business Continuity, version 2011. IBM. Retrieved 3 August 2012.
- ↑ [1] 'What is Business Continuity Management', DRI International, 2017
- ↑ "Information systems continuity process". March 2017. https://dl.acm.org/citation.cfm?id=3062955.
- ↑ "2017 IT Service Continuity Directory". Disaster Recovery Journal. https://www.drj.com/images/journal/fall-2017-volume30-issue3/2017_ITServiceDir.pdf.
- ↑ "Defending The Data Strata". December 24, 2013. https://www.forbesmiddleeast.com/en/defending-the-data-strata.
- ↑ "ISO 22301 to be published Mid May - BS 25999-2 to be withdrawn" (in en). 2012-05-03. https://www.continuityforum.org/content/news/165318/iso-business-continuity-standard-22301-replace-bs-25999-2.
- ↑ "ITIL glossary and abbreviations". https://www.axelos.com/glossaries-of-terms.
- ↑ 9.0 9.1 9.2 "Like The NFL Draft, Is The Clock The Enemy Of Your Recovery Time". Forbes. April 30, 2015. https://www.forbes.com/sites/sungardas/2015/04/30/like-the-nfl-draft-is-the-clock-the-enemy-of-your-recovery-time-objective.
- ↑ "Three Reasons You Can't Meet Your Disaster Recovery Time". Forbes. October 10, 2013. https://www.forbes.com/sites/sungardas/2013/10/29/three-reasons-you-cant-meet-your-disaster-recovery-time-objectives.
- ↑ 11.0 11.1 11.2 11.3 "Understanding RPO and RTO". DRUVA. 2008. http://www.druva.com/blog/2008/03/22/understanding-rpo-and-rto.
- ↑ 12.0 12.1 "How to fit RPO and RTO into your backup and recovery plans". https://searchstorage.techtarget.com/feature/What-is-the-difference-between-RPO-and-RTO-from-a-backup-perspective.
- ↑ "Clock... modifications
- ↑ Richard May. "Finding RPO and RTO". http://www.virtualdcs.co.uk/blog/business-continuity-planning-rpo-and-rto.html.
- ↑ "Data transfer and synchronization between mobile systems". May 14, 2013. http://www.freepatentsonline.com/8442943.html.
- ↑ "Amendment #5 to S-1". https://www.sec.gov/Archives/edgar/data/1519917/000119312512125661/d179347ds1a.htm. "real-time ... provide redundancy and back-up to ..."
- ↑ Peter H. Gregory (2011-03-03). "Setting the Maximum Tolerable Downtime -- setting recovery objectives". IT Disaster Recovery Planning For Dummies. Wiley. pp. 19–22. ISBN 978-1118050637. https://books.google.com/books?id=YC49DXW-_60C&pg=PA20.
- ↑ William Caelli; Denis Longley (1989). Information Security for Managers. Springer. p. 177. ISBN 1349101370. https://books.google.com/books?isbn=1349101370.
- ↑ "Catastrophe? It Can't Possibly Happen Here". The New York Times. January 29, 1995. https://www.nytimes.com/1995/01/29/business/catastrophe-it-can-t-possibly-happen-here.html. ".. patient records"
- ↑ "Commercial Property/Disaster Recovery". October 9, 1994. https://www.nytimes.com/1994/10/09/realestate/commercial-property-disaster-recovery-business-whose-clients-hope-never-use-it.html. "...the disaster-recovery industry has grown to"
- ↑ Charlie Taylor (June 30, 2015). "US tech firm Sungard announces 50 jobs for Dublin". The Irish Times. https://www.irishtimes.com/business/technology/us-tech-firm-sungard-announces-50-jobs-for-dublin-1.2267857. "Sungard .. founded 1978"
- ↑ Cassandra Mascarenhas (November 12, 2010). "SunGard to be a vital presence in the banking industry". Wijeya Newspapers Ltd.. http://www.ft.lk/it-telecom-tech/sungard-to-be-a-vital-presence-in-the-banking-industry/50-7581. "SunGard ... Sri Lanka's future."
- ↑ SecaaS Category 9 // BCDR Implementation Guidance CSA, retrieved 14 July 2014.
- ↑ "Threat and Hazard Identification and Risk Assessment (THIRA) and Stakeholder Preparedness Review (SPR): Guide Comprehensive Preparedness Guide (CPG) 201, 3rd Edition". US Department of Homeland Security. May 2018. https://www.fema.gov/media-library-data/1527613746699-fa31d9ade55988da1293192f1b18f4e3/CPG201Final20180525_508c.pdf.
- ↑ "Post-Disaster Recovery Planning Forum: How-To Guide, Prepared by Partnership for Disaster Resilience". University of Oregon's Community Service Center, (C) 2007, www.OregonShowcase.org. http://1.usa.gov/1IBkvv0.
- ↑ "The Importance of Disaster Recovery". http://www.techadvisory.org/2016/01/the-importance-of-disaster-recovery/.
- ↑ "IT Disaster Recovery Plan". FEMA. 25 October 2012. http://www.ready.gov/business/implementation/IT.
- ↑ "Use of the Professional Practices framework to develop, implement, maintain a business continuity program can reduce the likelihood of significant gaps". 2021-08-16. https://drii.org/resources/professionalpractices/EN.
- ↑ Gregory, Peter. CISA Certified Information Systems Auditor All-in-One Exam Guide, 2009. ISBN:978-0-07-148755-9. Page 480.
- ↑ Brandon, John (23 June 2011). "How to Use the Cloud as a Disaster Recovery Strategy". Inc.. http://www.inc.com/guides/201106/how-to-use-the-cloud-as-a-disaster-recovery-strategy.html. Retrieved 11 May 2013.
- ↑ "Disaster Recovery as a Service (DRaaS)". https://searchdisasterrecovery.techtarget.com/definition/disaster-recovery-as-a-service-DRaaS.
Further reading
- Barnes, James (2001). A guide to business continuity planning. Chichester, NY: John Wiley. ISBN 9780470845431. OCLC 50321216.
- Bell, Judy Kay (2000). Disaster survival planning : a practical guide for businesses. Port Hueneme, CA, US: Disaster Survival Planning. ISBN 9780963058027. OCLC 45755917.
- Fulmer, Kenneth (2015). Business Continuity Planning : a Step-by-Step Guide With Planning Forms. Brookfield, CT: Rothstein Associates, Inc. OCLC 712628907, 905750518, 1127407034. ISBN 9781931332804.
- DiMattia, Susan S (2001). "Planning for Continuity". Library Journal 126 (19): 32–34. ISSN 0363-0277. OCLC 425551440.
- Harney, John (July–August 2004). "Business Continuity and Disaster Recovery: Back Up Or Shut Down". http://www.edocmagazine.com/archives_articles.asp?ID=29114.
- "ISO 22301:2019(en), Security and resilience — Business continuity management systems — Requirements". ISO. https://www.iso.org/obp/ui/#iso:std:iso:22301:ed-2:v1:en.
- "ISO/IEC 27001:2013(en) Information technology — Security techniques — Information security management systems — Requirements". ISO. https://www.iso.org/obp/ui/#iso:std:iso-iec:27001:ed-2:v1:en.
- "ISO/IEC 27002:2013(en) Information technology — Security techniques — Code of practice for information security controls". ISO. https://www.iso.org/obp/ui/#iso:std:iso-iec:27002:ed-2:v1:en.
External links
- "Glossary of terms for Business Continuity, Disaster Recovery and related data mirroring & z/OS storage technology solutions". https://recoveryspecialties.com/glossary.html.
- "IT Disaster Recovery Plan". https://www.ready.gov/it-disaster-recovery-plan.
- "RPO (Recovery Point Objective) Explained". 2019-08-08. https://www.ibm.com/services/business-continuity/rpo.
 |