Copy detection pattern
A copy detection pattern (CDP)[1] or graphical code[2][3] is a small random or pseudo-random digital image which is printed on documents, labels or products for counterfeit detection. Authentication is made by scanning the printed CDP using an image scanner or mobile phone camera.[4] It is possible to store additional product-specific data into the CDP that will be decoded during the scanning process.[5] A CDP can also be inserted into a 2D barcode to facilitate smartphone authentication and to connect with traceability data.[6]
Principle
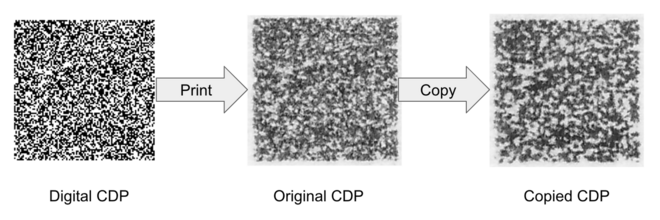
The detection of counterfeits using a CDP relies on an "information loss principle",[7] which states that every time a digital image is printed or scanned, some information about the original digital image is lost. A CDP is a maximum entropy image that attempts to take advantage of this information loss. Since producing a counterfeit CDP requires an additional scanning and printing processes, it will have less information than an original CDP. By measuring the information in the scanned CDP, the detector can determine whether the CDP is an original print or a copy.
CDPs aim to address limitations of optical security features such as security holograms. They are motivated by the need for security features that can be originated, managed and transferred digitally, and that are machine readable.[1] Contrarily to many traditional security printing techniques, CDPs do not rely on Security by Obscurity,[8] as the algorithm for generating CDPs can be public as long as the key used to generate it or the digital CDP is not revealed.[9]
CDPs have also been described as a type of optical physical unclonable function.[2] While they have been cited as a "powerful tool to detect copies",[10] it is noted however that CDPs "require an extensive knowledge of printing technologies"[11] because the printing process introduces variation that is foundational to copy detection.
Security assessment
The theoretical and practical assessment of the security level of CDPs, in other words the detector's ability to detect counterfeit attempts, is an ongoing area of research:
- In,[9] practical recommendations on printing stability, taking into account scanning quality of the detector, and managing the security of printing facilities.
- In,[12] a decision theoretic-model is developed to determine optimality properties of CDPs in idealised conditions. Based on an additive Gaussian noise assumption for the print channel and an attacker who takes optimal decisions, it is shown that the most effective decision function is a correlation function.
- In,[13] different new CDP detection metrics are proposed and confirmed a significant improvement of copy detection accuracy.
- In,[14] the impact of multiple printed observations of the same CDP is studied, and it is shown that the noise due to the printing process can be reduced but not completely removed, due to deterministic printing artefacts.
- In,[15] a theoretical comparison is made between the performance of CDPs and natural randomness.
- In [16] and,[17] deep learning methods are used to recover portions of the digital CDP, and it is shown that these can be used to launch clonability attacks.
- In,[18] quality control challenges are reviewed, and an inline verification system of secure graphics is proposed for high security printing applications.
- In,[19] different attack methods based on restoration of the scanned CDP are tested. and show that a classifier based on support vector domain description outperforms other classification methods.
Applications
CDPs are used for different physical item authentication applications:
- As a means of providing a product authentication service using the Internet of Things.[20][11]
- For securing identification documents, in combination with digital watermarks and 2D barcodes.[8] They were used in 2006 to protect identification badges during the FIFA World Cup.[21][22]
- Integrated into QR Codes to enable consumers to check product authenticity with a smartphone application.[23]
- For authenticating pharmaceutical packaging.[24]
Related techniques
The EURion constellation and digital watermarks are inserted into banknotes to be detected by scanners, photocopiers and image processing software. However the objective of these techniques is not to detect whether a given banknote is a counterfeit, but to deter amateur counterfeiters from reproducing banknotes by blocking the device or software used to make the counterfeit.[25]
Digital watermarks may be used as well to differentiate original prints from counterfeits.[26][27] A digital watermark may also be inserted into a 2D barcode.[28] The fundamental difference between digital watermarks and CDPs is that a digital watermark must be embedded into an existing image while respecting a fidelity constraint, while the CDP does not have such constraint.[29]
References
- ↑ 1.0 1.1 Picard, Justin (2004-06-03). Van Renesse, Rudolf L. ed. "Digital authentication with copy-detection patterns". Optical Security and Counterfeit Deterrence Techniques V (SPIE) 5310: 176. doi:10.1117/12.528055. Bibcode: 2004SPIE.5310..176P. https://www.researchgate.net/publication/253088312.
- ↑ 2.0 2.1 Phan Ho, Anh Thu; Mai Hoang, Bao An; Sawaya, Wadih; Bas, Patrick (2014-06-05). "Document authentication using graphical codes: reliable performance analysis and channel optimization" (in en). EURASIP Journal on Information Security 2014 (1): 9. doi:10.1186/1687-417X-2014-9. ISSN 1687-417X. https://www.researchgate.net/publication/270463004.
- ↑ Tkachenko, Iuliia; Puech, William; Destruel, Christophe; Strauss, Olivier; Gaudin, Jean-Marc; Guichard, Christian (2016-03-01). "Two-Level QR Code for Private Message Sharing and Document Authentication". IEEE Transactions on Information Forensics and Security 11 (3): 571–583. doi:10.1109/TIFS.2015.2506546. ISSN 1556-6021.
- ↑ Technology and Security: Countering Criminal Infiltrations in the Legitimate Supply Chain. United Nations Interregional Crime and Justice Research Institute. 2021. http://www.unicri.it/sites/default/files/2021-07/Technology%20and%20Security%20Countering%20Criminal%20Infiltrations%20in%20the%20Legitimate%20Supply%20Chain_1.pdf.
- ↑ Abele, Eberhard. (2011). Schutz vor Produktpiraterie : ein Handbuch für den Maschinen- und Anlagenbau. Ksuke, Philipp., Lang, Horst.. Berlin: Springer. ISBN 978-3-642-19280-7. OCLC 726826809. https://www.worldcat.org/oclc/726826809.
- ↑ EUIPO Anti-Counterfeiting Technology Guide. European Observatory on Infringements of Intellectual Property Rights. 2021. https://euipo.europa.eu/ohimportal/en/web/observatory/news/-/action/view/8550135.
- ↑ "Pagina iniziale dell'Ufficio Italiano Brevetti e Marchi - Copy Detection Patterns – CDP". https://uibm.mise.gov.it/index.php/it/225-lotta-alla-contraffazione/2036477-copy-detection-patterns-cdp.
- ↑ 8.0 8.1 Picard, Justin; Vielhauer, Claus; Thorwirth, Niels (2004-06-22). Delp Iii, Edward J; Wong, Ping W. eds. "Towards fraud-proof ID documents using multiple data hiding technologies and biometrics". Security, Steganography, and Watermarking of Multimedia Contents VI (SPIE) 5306: 416. doi:10.1117/12.525446. Bibcode: 2004SPIE.5306..416P.
- ↑ 9.0 9.1 Picard, Justin (2008). "Copy Detectable Images: From Theory to Practice". Conference on Optical Security and Counterfeit Deterrence 2008 1: 372–381. https://www.researchgate.net/publication/341030602.
- ↑ Dirik, Ahmet Emir; Haas, Bertrand (November 2012). "Copy detection pattern-based document protection for variable media". IET Image Processing 6 (8): 1102–1113. doi:10.1049/iet-ipr.2012.0297. ISSN 1751-9667. https://ieeexplore.ieee.org/document/6403957. Retrieved 12 August 2020.
- ↑ 11.0 11.1 Vision and challenges for realising the Internet of things. Sundmaeker, Harald., Guillemin, Patrick., Friess, Peter., Woelfflé, Sylvie., European Commission. Directorate-General for the Information Society and Media.. Luxembourg: EUR-OP. 2010. ISBN 978-92-79-15088-3. OCLC 847355368. https://www.worldcat.org/oclc/847355368.
- ↑ Picard, Justin (2008). "On the Security of Copy Detectable Images". NIP & Digital Fabrication Conference, 2008 International Conference on Digital Printing Technologies. https://www.researchgate.net/publication/341030510.
- ↑ Dirik, A. E.; Haas, B. (2012-11-01). "Copy detection pattern-based document protection for variable media" (in en). IET Image Processing 6 (8): 1102–1113. doi:10.1049/iet-ipr.2012.0297. ISSN 1751-9667.
- ↑ Baras, Cleo; Cayre, François (2012-08-01). "2D bar-codes for authentication: A security approach". 2012 Proceedings of the 20th European Signal Processing Conference (EUSIPCO): 1760–1766. https://ieeexplore.ieee.org/document/6334191.
- ↑ Voloshynovskiy, Slava; Holotyak, Taras; Bas, Patrick (2016-03-01). "Physical object authentication: Detection-theoretic comparison of natural and artificial randomness". 2016 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). IEEE. pp. 2029–2033. doi:10.1109/icassp.2016.7472033. ISBN 978-1-4799-9988-0. http://sip.unige.ch/articles/2016/2016.ICASSP.Final.PUF.pdf.
- ↑ Taran, Olga; Bonev, Slavi; Voloshynovskiy, Slava (2019-03-18). "Clonability of anti-counterfeiting printable graphical codes: a machine learning approach". arXiv:1903.07359 [cs.CR].
- ↑ Yadav, Rohit; Tkachenko, Iuliia; Trémeau, Alain; Fournel, Thierry (2019). "Estimation of Copy-sensitive Codes Using a Neural Approach". Proceedings of the ACM Workshop on Information Hiding and Multimedia Security. New York, New York, USA: ACM Press. pp. 77–82. doi:10.1145/3335203.3335718. ISBN 978-1-4503-6821-6. https://hal.archives-ouvertes.fr/hal-02330988/file/IH_MMSec_2019_final.pdf.
- ↑ Picard, Justin; Khatri, Nick; 100% Inline Verification of Secure Graphics at High Resolution; 2019-05-15; Digital Document Security; Reconnaissance International
- ↑ Zhang, Pei; Zhang, Weiming; Yu, Nenghai (April 2019). "Copy Detection Pattern-Based Authentication for Printed Documents with Multi-Dimensional Features". 2019 7th International Conference on Information, Communication and Networks (ICICN). IEEE. pp. 150–157. doi:10.1109/icicn.2019.8834939. ISBN 978-1-7281-0425-6.
- ↑ Chaves, Leonardo W. F.; Nochta, Zoltán (2010-07-12), "Breakthrough Towards the Internet of Things", Unique Radio Innovation for the 21st Century (Springer Berlin Heidelberg): pp. 25–38, doi:10.1007/978-3-642-03462-6_2, ISBN 978-3-642-03461-9, Bibcode: 2010urif.book...25C
- ↑ Yumpu.com. "FIFA World Cup Case Study - Code Corporation" (in en). https://www.yumpu.com/en/document/read/4033452/fifa-world-cup-case-study-code-corporation.
- ↑ "Pattern makes 2D barcodes copy-proof". 2009-07-15. https://www.securingindustry.com/pattern-makes-2d-barcodes-copy-proof/s15/a179/.
- ↑ Carron. "Combatting counterfeiting using QR codes". https://phys.org/news/2015-05-combatting-counterfeiting-qr-codes.html.
- ↑ "Digital and Analog Technologies for Product Authentication and Tamper Evidence" (in en-gb). 2019-03-28. https://packagingeurope.com/api/content/997c4c0a-515c-11e9-ada6-12f1225286c6/.
- ↑ "Software Detection of Currency // Dr Steven J. Murdoch". https://murdoch.is/projects/currency/.
- ↑ Mahmoud, Khaled W.; Blackledge, Jonathon M.; Datta, Sekharjit; Flint, James A. (2004-06-22). Delp Iii, Edward J.; Wong, Ping W.. eds. "Print protection using high-frequency fractal noise". Security, Steganography, and Watermarking of Multimedia Contents VI (SPIE) 5306: 446. doi:10.1117/12.526677. Bibcode: 2004SPIE.5306..446M.
- ↑ Zhou, Jifeng; Pang, Mingyong (September 2010). "Digital watermark for printed materials". 2010 2nd IEEE International Conference on Network Infrastructure and Digital Content. IEEE. pp. 758–762. doi:10.1109/icnidc.2010.5657884. ISBN 978-1-4244-6851-5.
- ↑ Nguyen, Hoai Phuong; Retraint, Florent; Morain-Nicolier, Frédéric; Delahaies, Angès (2019). "A Watermarking Technique to Secure Printed Matrix Barcode—Application for Anti-Counterfeit Packaging". IEEE Access 7: 131839–131850. doi:10.1109/ACCESS.2019.2937465. ISSN 2169-3536. Bibcode: 2019IEEEA...7m1839N.
- ↑ Barni, Mauro; Cox, Ingemar; Kalker, Ton et al., eds (2005) (in en-gb). Digital Watermarking. Lecture Notes in Computer Science. 3710. doi:10.1007/11551492. ISBN 978-3-540-28768-1.
External links
- Dataset of CDPs with copies on Kaggle
- Dataset of CDPs from the University of St-Etienne (for academic use only)
- Dataset of CDPs from University of Geneva
 |

