Engineering:Happy99
 | |
| Aliases | Ska, I-Worm |
|---|---|
| Type | Computer worm |
| Author(s) | "Spanska" |
| Port(s) used | 25, 119[1][2] |
| Operating system(s) affected | Windows 95, Windows 98, Windows NT[3] |
| Filesize | 10,000 bytes |
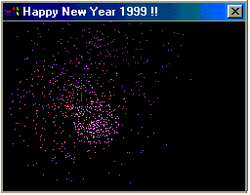
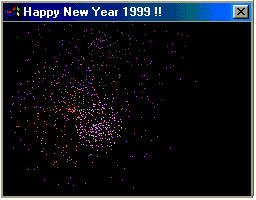
Happy99 (also termed Ska or I-Worm)[4] is a computer worm for Microsoft Windows. It first appeared in mid-January 1999, spreading through email and usenet. The worm installs itself and runs in the background of a victim's machine, without their knowledge. It is generally considered the first virus to propagate by email, and has served as a template for the creation of other self-propagating viruses. Happy99 has spread on multiple continents, including North America, Europe, and Asia.
Significance
Happy99 was described by Paul Oldfield as "the first virus to spread rapidly by email".[5] In the Computer Security Handbook, Happy99 is referred to as "the first modern worm".[6] Happy99 also served as a template for the creation of ExploreZip, another self-spreading virus.[7]
Spread
The worm first appeared on 20 January 1999.[8] Media reports of the worm started coming in from the United States and Europe, in addition to numerous complaints on newsgroups from users that had become infected with the worm.[9] Asia Pulse reported 74 cases of the virus from Japan in February, and 181 cases were reported in March—a monthly record at the time.[10][11] On 3 March 1999, a Tokyo job company accidentally sent 4000 copies of the virus to 30 universities in Japan.[12]
Dan Schrader of Trend Micro said that Happy99 was the single most commonly reported virus in their system for the month of March.[13] A virus bulletin published in February 2000 reported that Happy99 caused reports of file-infecting malware to reach over 16% in April 1999.[14] Sophos listed Happy99 among the top ten viruses reported in the year of 1999.[15] Eric Chien, head of research at Symantec, reported that the worm was the second most reported virus in Europe for 2000.[16] Marius Van Oers, a researcher for Network Associates, referred to Happy99 as "a global problem", saying that it was one of the most commonly reported viruses in 1999.[17] When virus researcher Craig Schmugar posted a fix for the virus on his website, a million people downloaded it.[18]
Technical details
The worm spreads through email attachments and Usenet.[19][20][21] When executed, animated fireworks and a "Happy New Year" message display.[19][22] The worm modifies Winsock, a Windows communication library, to allow itself to spread.[19] The worm then attaches itself automatically to all subsequent emails and newsgroup posts sent by a user.[23] The worm modifies a registry key to automatically start itself when the computer is rebooted. In some cases, the program may cause several error messages to appear.[24]
The worm was written by a French virus writer known as "Spanska". Other than propagating itself, the worm does no further damage to an infected computer.[25][26] The worm typically uses port 25 to spread, but uses port 119 if port 25 is not available.[24] The executable of the worm is 10,000 bytes in size; a list of spammed newsgroups and mail addresses is stored on the infected hard drive.[22][27] The worm spreads only if the Winsock library is not set to read-only.
See also
References
- ↑ Stephen Watkins; Gregg, Michael B. (2006). Hack the Stack: Using Snort and Ethereal to Master the 8 Layers of an Insecure Network. Syngress Publishing. pp. 407, 408. ISBN 1-59749-109-8.
- ↑ Davis, Peter (2002). Securing and controlling Cisco routers. Boca Raton: Auerbach Publications. pp. 621, 622. ISBN 0-8493-1290-6. https://archive.org/details/securingcontroll0000davi/page/621.
- ↑ George Skarbek (16 March 1999). "Tech talk - Happy99 Virus". The Courier-Mail.
- ↑ Roger A. Grimes (2001). Malicious Mobile Code: Virus Protection for Windows. Sebastopol, CA: O'Reilly. pp. 6. ISBN 1-56592-682-X. https://archive.org/details/maliciousmobilec00grim/page/6.
- ↑ Paul Oldfield (2001). Computer viruses demystified. Aylesbury, Bucks: Sophos. pp. 32. ISBN 0-9538336-0-7.
- ↑ Bosworth, Seymour; Kabay, Michel E. (2002). Computer security handbook. Chichester: John Wiley & Sons. pp. 44. ISBN 0-471-26975-1. https://archive.org/details/computersecurity4theunse/page/44.
- ↑ Rosie Lombardi (2 July 1999). "Microsoft's dominance plays a role". Computing Canada. http://www.itbusiness.ca/it/client/en/home/News.asp?id=27334.
- ↑ Ellis, Juanita; Korper, Steffano (2001). The E-commerce book: building the E-empire. San Diego: Academic. pp. 192. ISBN 0-12-421161-5. https://archive.org/details/unset0000unse_t5d8/page/192.
- ↑ David Watts (16 February 1999). "Help Desk". The West Australian.
- ↑ "251 Cases of Computer Virus Damage Reported in Japan in Feb". Asia Pulse. 7 March 1999.
- ↑ Makoto Ushida (19 April 1999). "Cyberslice - Experts warn of lurking computer viruses". Asahi Shimbun.
- ↑ "Virus-tainted e-mail sent to 4,000". The Daily Yomiuri. 6 June 1999.
- ↑ Clint Swett; Eric Young (7 April 1999). "Tech Talk Column". The Sacramento Bee.
- ↑ "Virus Bulletin". Virus Bulletin (Virus Bulletin Ltd.). 2000. ISSN 0956-9979.
- ↑ "Old viruses live on". Adelaide Advertiser. 19 February 2000.
- ↑ "Virus variants put users at risk Users are at risk from new variants of popular viruses which can evade some antivirus protection". World Reporter TM. 6 March 2000.
- ↑ Deborah Scoblionkov (2 March 1999). "Bigfoot Users Get a Hotfoot". Wired. https://www.wired.com/science/discoveries/news/1999/03/18208. Retrieved 7 March 2017.
- ↑ Jeffrey Kosseff (15 September 2003). "Virus-Hunters Scour Internet with 'Dirty' Computers". The Oregonian.
- ↑ 19.0 19.1 19.2 Chen, William W. L. (2005). Statistical methods in computer security. New York, N.Y: Marcel Dekker. pp. 272. ISBN 0-8247-5939-7.
- ↑ Michael J. Isaac; Isaac, Debra S. (2003). The SSCP prep guide: mastering the seven key areas of system security. New York: Wiley. pp. 0471273511. ISBN 0-471-27351-1.
- ↑ Roberta Fusaro (29 January 1999). "Internet worm can crash corporate servers". CNN. http://www.cnn.com/TECH/computing/9901/29/iworm-ent.idg/index.html.
- ↑ 22.0 22.1 Rubin, Aviel D. (2001). White-hat security arsenal: tackling the threats. Boston: Addison-Wesley. pp. 31. ISBN 0-201-71114-1. https://archive.org/details/whitehatsecurity00avie/page/31.
- ↑ Carrie Kirby (22 December 2000). "Holiday E-Mail Gives Viruses An Opportunity". San Francisco Chronicle.
- ↑ 24.0 24.1 Grover, Amit (August 2003). Application Adaptive Bandwidth Management Using Real-Time Network Monitoring. pp. 77–78. Archived from the original on 14 September 2006. https://web.archive.org/web/20060914091249/http://etd-submit.etsu.edu/etd/theses/available/etd-0715103-211816/unrestricted/GroverA071803f.pdf. Retrieved 27 March 2009.
- ↑ Knittel, Brian; Cowart, Robert; Cowart, Bob (1999). Using MicroSoft Windows 2000 professional. Indianapolis, Ind: Que. pp. 936. ISBN 0-7897-2125-2. https://archive.org/details/usingmicrosoftwi00cowa/page/936.
- ↑ Trefor Roscoe (2004). Rapid Reference to Computers: Rapid Reference Series. St. Louis: Mosby. pp. 38. ISBN 0-7234-3357-7.
- ↑ Bob Sullivan (27 January 1999). "Happy99.exe worm spreads on Net". ZDNet. http://news.zdnet.com/2100-9595_22-101463.html?legacy=zdnn.
External links
 |
