Engineering:Mobile Signature Service
Mobile Signature Service (MSS) is a high-level service specified by the European Telecommunications Standards Institute that defines the roles participating in mobile identity management and mobile signature transactions, as well as functional and business-related requirements and interfaces.[1] The specification is the governing standard for PKI and enables cross-compatible mobile signature solutions.[2]
Background
The mobile signature services industry began in the early 2000s, with the release of the European Telecommunications Standards Institute (ETSI) mobile commerce standards (ETSI 102 203, 102 204, 102 206 and 102 207). The standards defined mobile signature as a universal method for using a mobile device to confirm the intention of a citizen to proceed with a transaction (digitally sign transactions on their mobile devices, turning the mobile device into personal trusted devices.) and mobile signature service as a facility that coordinates and manages the mobile signature process.[3]
Roles
Mobile user
The mobile user is either a private person in possession of the mobile device, or a device embedded in the mobile device to which a mobile signature is associated.[4]
Application provider
The application provider (AP) provides the service that the mobile user wishes to authenticate themselves to or the contract that the user wishes to sign.[4][5]
Smart card issuer
The smart card issuer, typically a mobile network operator, issues the mobile user with a smart card that is in some form capable of completing signature operations and on-board key generation. The issuer associates itself with an MSSP.[4][5]
Registration authority
The registration authority (RA), typically a mobile network operator, is in charge of registering Mobile Users to MSS.[4][5]
Certificate authority
The certificate authority (CA) is a service, typically a third party, that issues digital certificates to the mobile user's public key.[4][6][5]
Mobile signature service provider
The mobile signature service provider (MSSP) is a service that facilitates the communication between the AP and the mobile user's SIM card. The MSSP of the ETSI specification typically consists of a HomeMSSP, AE (acquiring entity) MSSP and possibly an RE (routing entity). APs connect to a HomeMSSP via AE MSSPs. HomeMSSPs connect to the mobile user's SIM card directly.[7][4][5]
Establishing a mobile identity
When a Mobile User subscribes to a Mobile Signature Service, the RA confirms their identity and binds their identity to a key pair as per public key infrastructure. The keys can be generated server-side or on the User's SIM card with On-Board Key Generation. With OBKG, the SIM card generates the key pair, sends the public key to the MSSP to be bound by the RA and certified by the CA, and has the Mobile User assign a signing PIN on the private key, which begins its existence on and never leaves the SIM card.[8][6]
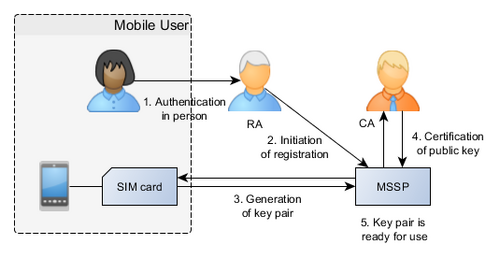
Completing a signature transaction
When a mobile user accesses an AP's service and wishes to perform a mobile signature, the AP sends a signature request to the mobile user's HomeMSSP via an AE MSSP. The MSSP forwards the AP's request to the mobile user's SIM card. Upon receiving the signature request, the mobile user's SIM card can only complete the signature when the mobile user gives their signing PIN. The requested data is signed with the mobile user's private key and sent back to the mobile user's HomeMSSP, which then returns the signature to the AP, who can verify it with the mobile user's public key.[9][6][10]

Roaming
The ETSI mobile commerce standard TS 102 207 defines a roaming framework between multiple MSS systems.[11] If the AP and Mobile User's HomeMSSPs are different, the AP's MSSP can reach the Mobile User's by roaming.[12]
This way, an AP can make a contract with any of the MSS system operators provide a service for all Mobile Users in the MSS mesh.
Revoking an identity
If at any point there is reason to believe that the user's mobile identity is at risk, they may ask the mobile network operator to have the CA revoke their certificate. Revoking the certificate of a user's public key makes the key pair unusable. Commonly, a revoked certificate cannot be reinstated remotely. Instead, a user must re-register in person in order to resume the use of MSS.[13]
References
- ↑ Venho, Joonas. "Mobile Signature Service Integration". Metropolia University of Applied Sciences. https://www.theseus.fi/bitstream/handle/10024/46982/MSS_integration.pdf?sequence=1.
- ↑ "When eID becomes Mobile for a whole nation". Valimo. http://www.gemalto.com/brochures-site/download-site/Documents/gov_cs_finland_valimo.pdf.
- ↑ "Mobile Signature Service Provider". https://www.methics.fi/docs/Methics_MSSP_ServiceProvider_study.pdf.
- ↑ 4.0 4.1 4.2 4.3 4.4 4.5 ETSI TR 102 203 V1.1.1 (2003-05) ch. 12
- ↑ 5.0 5.1 5.2 5.3 5.4 Ruiz-Martínez, Antonio; Sánchez-Martinez, Daniel; Mártinez-Montesinos, María; Gómez-Skarmeta, Antonio (15 October 2007). "A Survey of Electronic Signature Solutions in Mobile Devices". Journal of Theoretical and Applied Electronic Commerce Research 2 (3): 105.
- ↑ 6.0 6.1 6.2 Saarinen, Jyrki. "Julkisen avaimen menetelmä ja ETSI:n MSS-määritys" (in fi). Helsingin yliopisto - Tietojenkäsittelytieteen laitos. https://helda.helsinki.fi/bitstream/handle/10138/21462/julkisen.pdf?sequence=2.
- ↑ ETSI TS 102 207 p. 14 ch. 6.2
- ↑ ETSI TR 102 203 V1.1.1 p. 46 ch. 13.2.1
- ↑ ETSI TR 102 203 V1.1.1 p. 47 ch. 13.2.2
- ↑ "Mobile signature - Siso trial". Orange. http://www.renewinghealth.eu/c/document_library/get_file?uuid=8b416b09-5e14-4ad5-8c70-a6dcd2201da0&groupId=28946.
- ↑ Kerttula, Esa (4 July 2015). "A novel federated strong mobile signature service — The Finnish case" (in en). Journal of Network and Computer Applications 56 (56): 14. ISSN 1084-8045.
- ↑ ETSI TR 102 203 V1.1.1 p. 48 ch. 13.2.3
- ↑ ETSI TR 102 203 V1.1.1 p. 34 ch. 10.6
 |
