Software:LogMeIn Hamachi
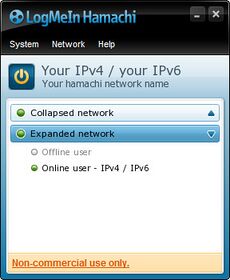 Screenshot of the Hamachi Client, showing a joined network and other users who are participating | |
| Original author(s) | Alex Pankratov |
|---|---|
| Developer(s) | LogMeIn Inc. |
| Stable release | 2.3.0.78 (Windows)[1]
/ May 19, 2022 |
| Operating system | Microsoft Windows (XP or later), macOS, Linux, Linux on ARM (beta) |
| Type | P2P, VPN |
| License | Proprietary (Free of charge for up to 5 devices) |
| Website | www.vpn.net |
LogMeIn Hamachi is a virtual private network (VPN) application developed and released in 2004 by Alex Pankratov.[2][3] It is capable of establishing direct links between computers that are behind network address translation (NAT) firewalls without requiring reconfiguration (when the user's PC can be accessed directly without relays from the Internet/WAN side). Like other VPNs, it establishes a connection over the Internet that emulates the connection that would exist if the computers were connected over a local area network (LAN).
Hamachi became a LogMeIn product after the acquisition of Applied Networking Inc. in 2006.[2][4][5][6] It is currently available as a production version for Microsoft Windows and macOS, as a beta version for Linux, and as a system-VPN-based client compatible with Android and iOS.[7]
For paid subscribers Hamachi runs in the background on idle computers. The feature was previously available to all users but became restricted to paid subscribers only as of November 19, 2012.[8]
Operational summary
Hamachi is a proprietary centrally-managed VPN system, consisting of the server cluster managed by the vendor of the system and the client software, which is installed on end-user devices. Client software adds a virtual network interface to a computer, and it is used for intercepting outbound as well as injecting inbound VPN traffic. Outbound traffic sent by the operating system to this interface is delivered to the client software, which encrypts and authenticates it and then sends it to the destination VPN peer over a specially initiated UDP connection. Hamachi currently handles tunneling of IP traffic including broadcasts and multicast. The Windows version also recognizes and tunnels IPX traffic.
Each client establishes and maintains a control connection to the server cluster. When the connection is established, the client goes through a login sequence, followed by the discovery process and state synchronization. The login step authenticates the client to the server and vice versa. The discovery is used to determine the topology of the client's Internet connection, specifically to detect the presence of NAT and firewall devices on its route to the Internet. The synchronization step brings a client's view of its private networks in sync with other members of these networks.
When a member of a network goes online or offline, the server instructs other network peers to either establish or tear down tunnels to the former. When establishing tunnels between the peers, Hamachi uses a server-assisted NAT traversal technique, similar to UDP hole punching. Detailed information on how it works has not been made public. This process does not work on certain combinations of NAT devices, requiring the user to explicitly set up a port forward. Additionally 1.0 series of client software are capable of relaying traffic through vendor-maintained 'relay servers'.
In the event of unexpectedly losing a connection to the server, the client retains all its tunnels and starts actively checking their status. When the server unexpectedly loses client's connection, it informs client's peers about the fact and expects them to also start liveliness checks. This enables Hamachi tunnels to withstand transient network problems on the route between the client and the server as well as short periods of complete server unavailability. Some Hamachi clients also get closed port on other clients, which cannot be repaired by port forwarding.
Hamachi is frequently used for gaming and remote administration. The vendor provides free basic service, and extra features for a fee.
In February 2007, an IP-level block was imposed by Hamachi servers on parts of Vietnamese Internet space due to "the scale of the system abuse originating from blocked addresses". The company is working on a less intrusive solution to the problem.[citation needed]
Addressing
Each Hamachi client is normally assigned an IP address when it logs into the system for the first time. To avoid conflicting with existing private networks on the client side the normal private IP address blocks 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16 are not used.
Before November 19, 2012, the 5.0.0.0/8 range was used. This range was previously un-allocated but was allocated to RIPE NCC in late 2010 and space from this range is now being used by hosting providers on the public internet. Hamachi switched to the 25.0.0.0/8 block.[9]
The 25.0.0.0/8 block is allocated to the British Ministry of Defence. Organizations who need to communicate with the MOD may experience problems when more specific Internet routes attract traffic that was meant for internal hosts, or alternatively find themselves unable to reach the legitimate users of those addresses because those addresses are being used internally,[10] and such "squatting" is against the established practice of the Internet.
The client now supports IPv6, and if this is selected then the address assigned is picked from a range registered to LogMeIn.[9]
The IP address assigned to the Hamachi client is henceforth associated with the client's public crypto key. As long as the client retains its key, it can log into the system and use this IP address. Hamachi creates a single broadcast domain between all clients. This makes it possible to use LAN protocols that rely on IP broadcasts for discovery and announcement services over Hamachi networks.
Security
The following considerations apply to Hamachi's use as a VPN application:
- Additional risk of disclosure of sensitive data which is stored or may be logged by the mediation server — minimal where data is not forwarded.
- The security risks due to vulnerable services on remote machines otherwise not accessible behind a firewall, common to all VPNs.
- Hamachi is stated to use strong, industry-standard algorithms to secure and authenticate the data and its security architecture is open. Despite this, security cannot necessarily be guaranteed.[11]
- The existing client-server protocol documentation contains a number of errors,[12][13] some of which have been confirmed by the vendor, pending correction,[14] with others not yet confirmed.
- For the product to work, a "mediation server", operated by the vendor, is required.
- This server stores the nickname, maintenance password, statically-allocated 25.0.0.0/8 IP address and the associated authentication token of the user. As such, it can potentially log actual IP addresses of the VPN users as well as various details of the session.
Compatibility
The current builds of Hamachi are available for the following operating systems:[7]
- Microsoft Windows[15] (Windows 7 or later)
- macOS[15] (Mac OS X 10.6 or newer, which run only on x86, not PowerPC or Apple Silicon (ARM).)
- Linux (officially supported on Ubuntu 16.04 or newer / CentOS 7.2 or newer - x86/x64, beta armel/armhf versions available) Note: Stability issues on Ubuntu 20.04 LTS.[16]
- FreeBSD users can install and utilize Linux version, there's a port created in FreeBSD Ports.
- iOS (via iOS system VPN)
- Android (via Android system VPN, Android 11 or earlier)
Prior to versions 1.0.2.0 and 1.0.2.1 for the Windows release,[17][failed verification] many Windows Vista users had experienced compatibility and connection issues while using Hamachi. As of March 30, 2007, the software now includes Vista tweaks, which answer these OS-related problems, among other specific solutions.[18][failed verification]
See also
- Network address translation (NAT), as defined in RFC 3022
- Pertino
- Private network, as defined in RFC 1918
- Session Traversal Utilities for NAT (STUN), as defined in RFC 8489
- UDP hole punching, another NAT traversal technique
- Virtual Private LAN Service, as defined in RFC 4761 and 4762
- XLink Kai
References
- ↑ "What's new in Hamachi"
- ↑ 2.0 2.1 , Alexandre"Server-mediated setup and maintenance of peer-to-peer client computer communications" patent US20070157303A1, issued 2007-07-05
- ↑ "Hamachi: The virtual private networking system". Personal website of Alex Pankratov. https://swapped.cc/#!/hamachi.
- ↑ "REGISTRATION STATEMENT UNDER THE SECURITIES ACT OF 1933 LOGMEIN, INC.". January 11, 2008. https://www.sec.gov/Archives/edgar/data/1420302/000095013508000171/b67378lmsv1.htm. "On July 26, 2006, the Company purchased substantially all of the assets of Applied Networking, a Canadian corporation, in order to expand the Company’s product and service offerings and customer base. In connection with the acquisition, the Company acquired the patented Hamachi technology, a virtual private networking service."
- ↑ "Hamachi : Stay Connected". https://web.archive.org/web/20060828184025if_/http://hamachi.cc/.
- ↑ "LogMeIn Launches Instant, Zero Configuration VPN". October 31, 2006. http://corp.logmein.com/pdf/LMIPR_LMI_Hamachi.pdf.
- ↑ 7.0 7.1 "Hamachi System Requirements - Hamachi Support" (in en). https://support.logmeininc.com/hamachi/help/hamachi-system-requirements-hamachi-c-hamachi-systemrequirements.
- ↑ "CHANGES TO HAMACHI ON NOVEMBER 19TH". November 7, 2012. https://blog.logmein.com/products/changes-to-hamachi-on-november-19th.
- ↑ 9.0 9.1 "Changes to Hamachi on November 19th" , Official LogMeIn product blog
- ↑ Vegoda, Leo. "Used but Unallocated: Potentially Awkward /8 Assignments". The Internet Protocol Journal — Volume 10, No. 3. Cisco.com. http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_10-3/103_awkward.html.
- ↑ (in en) Hamachi Security, An Overview. LogMeIn, Inc.. 2015.
- ↑ Hamachi protocol documentation errors. Hamachi.cc forums.[|permanent dead link|dead link}}]
- ↑ More Hamachi protocol documentation concerns. Hamachi.cc forums.[|permanent dead link|dead link}}]
- ↑ Acknowledgement of documentation errors. Hamachi.cc forums.[|permanent dead link|dead link}}]
- ↑ 15.0 15.1 "Hamachi by LogMeIn Review" (in en). 28 October 2023. https://www.techradar.com/reviews/hamachi-by-logmein.
- ↑ "Hamachi randomly disconnects on Ubuntu 20.04". Community.logmein.com. https://community.logmein.com/t5/LogMeIn-Hamachi-Discussions/Hamachi-randomly-disconnects-on-Ubuntu-20-04/td-p/222430.
- ↑ "Hamachi for Windows, change log". Hamachi.cc. http://www.hamachi.cc/changes/.
- ↑ "Hamachi Community Forums - 1.0.2.1 is released". Forums.hamachi.cc. http://forums.hamachi.cc/viewtopic.php?t=13746.
External links
 |
