Universal 2nd Factor
Universal 2nd Factor (U2F) is an open standard that strengthens and simplifies two-factor authentication (2FA) using specialized Universal Serial Bus (USB), near-field communication (NFC), or Bluetooth Low Energy (BLE) devices based on similar security technology found in smart cards.[1][2][3][4][5] It is succeeded by the FIDO2 Project, which includes the W3C Web Authentication (WebAuthn) standard and the FIDO Alliance's Client to Authenticator Protocol 2 (CTAP2).[6]
While initially developed by Google and Yubico, with contribution from NXP Semiconductors, the standard is now hosted by the FIDO Alliance.[7][8]
This section contains a pro and con list, which is sometimes inappropriate. (April 2023) |
While time-based one-time password (TOTPs) (e.g. 6-digit codes generated on Google Authenticator) were a significant improvement over SMS-based security codes, a number of security vulnerabilities were still possible to exploit, which U2F sought to improve. Specifically:
| Issue | TOTP | U2F |
|---|---|---|
| Shared secret |
|
|
| Man-in-the-middle attack |
|
|
| Convenience / eavesdropping |
|
|
In terms of disadvantages, one significant difference and potential drawback to be considered regarding hardware-based U2F solutions is that unlike with TOTP shared-secret methods, there is no possibility of "backing up" recovery codes or shared secrets. If a hardware duplicate or alternative hardware key is not kept and the original U2F hardware key is lost, no recovery of the key is possible (because the private key exists only in hardware). Therefore, for services that do not provide any alternative account recovery method, the use of U2F should be carefully considered.
Design
The USB devices communicate with the host computer using the human interface device (HID) protocol, essentially mimicking a keyboard.[9] This avoids the need for the user to install special hardware driver software in the host computer and permits application software (such as a browser) to directly access the security features of the device without user effort other than possessing and inserting the device. Once communication is established, the application exercises a challenge–response authentication with the device using public-key cryptography methods and a secret unique device key manufactured into the device.[10]
Vulnerabilities
The device key is vulnerable to malicious manufacturer duplication.[11]
In 2020, independent security researchers found a method to extract private keys from Google Titan Key, a popular U2F hardware security token.[12][13][14] The method required physical access to the key for several hours, several thousand euros-worth of equipment, and was destructive to the plastic case of the key.[12][13][14] The attackers concluded that the difficulty of the attack meant that people were still safer to use the keys than not.[12][13][14] The attack was possible due to a vulnerability in the A700X microchip made by NXP Semiconductors, which is also used in security tokens made by Feitian and Yubico, meaning that those tokens are also vulnerable.[12][15] The vulnerability was responsibly disclosed to the affected manufacturers so that it might be fixed in future products.[12][13][14]
Support and use
U2F security keys are supported by Google Chrome since version 38,[2] Firefox since version 57[16] and Opera since version 40. U2F security keys can be used as an additional method of two-step verification on online services that support the U2F protocol, including Google,[2] Azure,[17] Dropbox,[18] GitHub,[19] GitLab,[20] Bitbucket,[21] Nextcloud,[22] Facebook,[23] and others.[24]
Chrome, Firefox, and Opera were, as of 2015[update], the only browsers supporting U2F natively. Microsoft has enabled FIDO 2.0 support for Windows 10's Windows Hello login platform.[25] Microsoft Edge[26] browser gained support for U2F in the October 2018 Windows Update. Microsoft accounts, including Office 365, OneDrive, and other Microsoft services, do not yet have U2F support. Mozilla has integrated it into Firefox 57, and enabled it by default in Firefox 60[27][28][29][30] and Thunderbird 60.[31] Microsoft Edge starting from build 17723 support FIDO2.[32] As of iOS and iPadOS 13.3 Apple now supports U2F in the Safari browser on those platforms.
Specifications
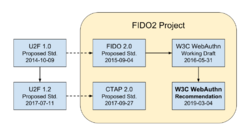
The U2F standard has undergone two major revisions:
Additional specification documents may be obtained from the FIDO web site.[35]
The U2F 1.0 Proposed Standard (October 9, 2014) was the starting point for a short-lived specification known as the FIDO 2.0 Proposed Standard (September 4, 2015). The latter was formally submitted to the World Wide Web Consortium (W3C) on November 12, 2015.[36] Subsequently, the first Working Draft of the W3C Web Authentication (WebAuthn) standard was published on May 31, 2016. The WebAuthn standard has been revised numerous times since then, becoming a W3C Recommendation on March 4, 2019.
Meanwhile the U2F 1.2 Proposed Standard (April 11, 2017) became the starting point for the Client to Authenticator Protocol (CTAP) Proposed Standard, which was published on September 27, 2017. FIDO CTAP complements W3C WebAuthn, both of which are in scope for the FIDO2 Project.
References
- ↑ Turner, Adam (November 5, 2014). "Google security keys may offer extra layer of online protection". The Sydney Morning Herald. Fairfax Media. http://www.smh.com.au/digital-life/consumer-security/google-security-keys-may-offer-extra-layer-of-online-protection-20141105-11dmca.html.
- ↑ 2.0 2.1 2.2 "What browsers support U2F?". Yubico. https://www.yubico.com/support/knowledge-base/categories/articles/browsers-support-u2f/.
- ↑ Bradley, Tony (October 21, 2014). "How a USB key drive could remove the hassles from two-factor authentication". PCWorld. IDG Consumer & SMB. http://www.pcworld.com/article/2836692/how-the-fido-alliances-u2f-could-simplify-two-factor-authentication.html#tk.rss_all.
- ↑ "FIDO Universal 2nd Factor". Yubico AB. https://www.yubico.com/applications/fido/.
- ↑ Diallo, Amadou (November 30, 2013). "Google Wants To Make Your Passwords Obsolete". Forbes. https://www.forbes.com/sites/amadoudiallo/2013/11/30/google-wants-to-make-your-passwords-obsolete/.
- ↑ "An In-Depth Guide to FIDO Protocols: U2F, UAF, and WebAuthn (FIDO2)". https://blog.strongkey.com/blog/guide-to-fido-protocols-u2f-uaf-webauthn-fido2.
- ↑ "FIDO Alliance – download specifications". FIDO Alliance. December 23, 2014. https://fidoalliance.org/download/.
- ↑ Krebs, Brian (October 14, 2014). "Google Accounts Now Support Security Keys". Krebs on Security. http://krebsonsecurity.com/2014/10/google-accounts-now-support-security-keys/#more-28412.
- ↑ "FIDO U2F HID Protocol Specification". October 9, 2014. https://fidoalliance.org/specs/fido-u2f-v1.0-ps-20141009/fido-u2f-hid-protocol-ps-20141009.html.
- ↑ "Key generation". Yubico. https://developers.yubico.com/U2F/Protocol_details/Key_generation.html.
- ↑ "Making identical U2F hardware security keys". June 27, 2024. https://www.malgregator.com/post/u2f/.
- ↑ 12.0 12.1 12.2 12.3 12.4 "Hackers can clone Google Titan 2FA keys using a side channel in NXP chips". January 8, 2021. https://arstechnica.com/information-technology/2021/01/hackers-can-clone-google-titan-2fa-keys-using-a-side-channel-in-nxp-chips/.
- ↑ 13.0 13.1 13.2 13.3 Cimpanu, Catalin (January 8, 2021). "New side-channel attack can recover encryption keys from Google Titan security keys". https://www.zdnet.com/article/new-side-channel-attack-can-recover-encryption-keys-from-google-titan-security-keys/.
- ↑ 14.0 14.1 14.2 14.3 "Researchers Show Google's Titan Security Keys Can Be Cloned". January 11, 2021. https://www.securityweek.com/researchers-show-googles-titan-security-keys-can-be-cloned.
- ↑ "Google Titan security keys hacked by French researchers". https://nakedsecurity.sophos.com/2021/01/11/google-titan-security-keys-hacked-by-french-researchers/.
- ↑ J.C. Jones (April 4, 2019). "Backward-Compatibility FIDO U2F support shipping soon in Firefox". Mozilla Security Blog. https://blog.mozilla.org/security/2019/04/04/shipping-fido-u2f-api-support-in-firefox/.
- ↑ "Passwordless authentication options for Azure Active Directory". https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-passwordless#fido2-security-keys.
- ↑ Heim, Patrick; Patel, Jay (August 12, 2015). "Introducing U2F support for secure authentication". https://blogs.dropbox.com/dropbox/2015/08/u2f-security-keys/.
- ↑ Olsen, Risk (October 1, 2015). "GitHub supports Universal 2nd Factor authentication". GitHub. https://github.com/blog/2071-github-supports-universal-2nd-factor-authentication.
- ↑ Nwaigwe, Amara (June 22, 2016). "Support for Universal 2nd Factor Authentication". https://about.gitlab.com/2016/06/22/gitlab-adds-support-for-u2f/.
- ↑ Kells, TJ (June 22, 2016). "Universal 2nd Factor (U2F) now supported in Bitbucket Cloud". https://blog.bitbucket.org/2016/06/22/universal-2nd-factor/.
- ↑ "Nextcloud 11 sets new standard for security and scalability". Nextcloud. December 13, 2016. https://nextcloud.com/blog/nextcloud-11-sets-new-standard-for-security-and-scalability.
- ↑ "Security Key for safer logins with a touch". Facebook. https://www.facebook.com/notes/facebook-security/security-key-for-safer-logins-with-a-touch/10154125089265766.
- ↑ "USB-Dongle Authentication". Josh Davis. http://www.dongleauth.com/.
- ↑ Ingalls, Dustin (February 13, 2015). "Microsoft Announces FIDO Support Coming to Windows 10". https://blogs.windows.com/business/2015/02/13/microsoft-announces-fido-support-coming-to-windows-10/.
- ↑ "Microsoft Edge now supports passwordless sign-ins" (in en-US). Engadget. https://www.engadget.com/2018/07/31/microsoft-edge-now-supports-passwordless-sign-ins/.
- ↑ "Firefox 57 has native support for U2F". https://addons.mozilla.org/en-GB/firefox/addon/u2f-support-add-on/reviews/920895/.
- ↑ "U2F Support Addon". https://addons.mozilla.org/en-US/firefox/addon/u2f-support-add-on/.
- ↑ "Firefox Nightly enables support for FIDO U2F Security Keys". September 22, 2017. https://www.yubico.com/2017/09/firefox-nightly-enables-support-fido-u2f-security-keys/.
- ↑ "Firefox 60.0 release notes". https://www.mozilla.org/en-US/firefox/60.0/releasenotes/.
- ↑ "Thunderbird 60.0 release notes". https://www.thunderbird.net/en-US/thunderbird/60.0beta/releasenotes/.
- ↑ "Introducing Web Authentication in Microsoft Edge — Microsoft Edge Dev BlogMicrosoft Edge Dev Blog" (in en-US). July 30, 2018. https://blogs.windows.com/msedgedev/2018/07/30/introducing-web-authentication-microsoft-edge/.
- ↑ "FIDO U2F V1.0 Proposed Standard 2014-10-09". FIDO Alliance. October 9, 2014. https://fidoalliance.org/specs/fido-u2f-v1.0-ps-20141009/.
- ↑ "FIDO U2F V1.2 Proposed Standard 2017-04-11". FIDO Alliance. April 11, 2017. https://fidoalliance.org/specs/fido-u2f-v1.2-ps-20170411/.
- ↑ "Download Specifications". FIDO Alliance. December 23, 2014. https://fidoalliance.org/specifications/download/.
- ↑ "Submission Request to W3C: FIDO 2.0 Platform Specifications 1.0". World Wide Web Consortium. https://www.w3.org/Submission/2015/02/.
Cite error: <ref> tag with name "W3C-WebAuthn-Level-1" defined in <references> is not used in prior text.
Cite error: <ref> tag with name "Auto58-22" defined in <references> is not used in prior text.
<ref> tag with name "Auto58-23" defined in <references> is not used in prior text.
 |
