Hacking: The Art of Exploitation
Hacking: The Art of Exploitation (ISBN:1-59327-007-0) is a book by Jon "Smibbs" Erickson about computer security and network security.[1] It was published by No Starch Press in 2003,[2][3] with a second edition in 2008.[4][5] All of the examples in the book were developed, compiled, and tested on Gentoo Linux. The book also comes with a CD that contains a Linux environment with all the tools and examples used in the book.
Background information
Jon "Smibbs" Erickson worked in the field of computer security with a background in computer science.[6] As of 2011, he worked as a vulnerability researcher and computer security specialist in northern California. A bootable CD is included with the book which provides a Linux-based programming and debugging environment for the users.
Content of 1st edition
The content of Exploiting (2003) moves between programming, networking, and cryptography. The book does not use any notable measure of real-world examples; discussions rarely bring up specific worms and exploits.
Programming
The computer programming portion of Hacking takes up over half of the book. This section goes into the development, design, construction, and testing of exploit code, and thus involves some basic assembly programming. The demonstrated attacks range from simple buffer overflows on the stack to techniques involving overwriting the Global Offset Table.
While Erickson discusses countermeasures such as a non-executable stack and how to evade them with return-to-libc attacks, he does not dive into deeper matters without known guaranteed exploits such as address space layout randomization. The book also does not cover the Openwall, GrSecurity, and PaX projects, or kernel exploits.
Networking
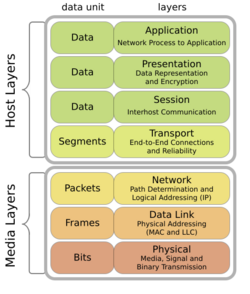
The networking segment of Hacking explains the basics of the OSI model and basic networking concepts, including packet sniffing, connection hijacking, denial of service, and port scanning.
Cryptology
The cryptology section of Hacking covers basic information theory, in addition to symmetric and asymmetric encryption. It winds out in cracking WEP utilizing the Fluhrer, Mantin, and Shamir attacks. Besides the basics, including man-in-the-middle attacks, dictionary attacks, and the use of John the Ripper; Hacking discusses quantum key distribution, Lov Grover's Quantum Search Algorithm, and Peter Shor's Quantum Factoring Algorithm for breaking RSA encryption using a very large quantum computer.
Other details
The front cover of Hacking shows the complete process, from reverse engineering to carrying out the attack, of developing an exploit for a program that is vulnerable to buffer overflow in its command-line arguments.
Content of 2nd edition
 | |
| Author | Jon Erickson |
|---|---|
| Country | United States (Original) |
| Language | English (Second Edition) |
| Series | Second Edition |
| Genre | Computer Science |
| Publisher | No Starch Press |
Publication date | February 2008 |
| Media type | Print Paperback |
| Pages | 488 |
| ISBN | ISBN:978-1593271442 |
The content of Hacking: The Art of Exploitation Second Edition (2008), the introduction of the book states that hacking should only be done within the confines of the law, and only for productive reasons. Below are the chapters:
0x200 Programming
The chapter covers control structures and other basic aspects of programming.
0x300 Exploitation
This chapter covers exploit techniques such as memory corruption, Buffer overflows and format strings, especially using Perl and Bash shellcode.
0x400 Networking
OSI Model
In communication among computers through networking, the OSI Model is used. This model provides the standards that computers use to communicate. The OSI Model is described in the book.
0x500 Shellcode
Shellcode is a custom code written by a hacker for execution upon gaining control over a program.
0x600 Countermeasures
This part of the book is about having defenses and intrusion prevention systems to stop known hacking exploits.
0x700 Cryptology
See also
References
- ↑ "Book Review: Hacking". 25 July 2004. http://www.unixreview.com/documents/s=9181/ur0406o/.
- ↑ Bruen, Robert (March 15, 2004). "Robert Bruen's review of "Hacking. The Art of Exploitation" by Jon Erikson, No Starch Press 2003, IEEE Cipher, E59 Mar 15, 2004". https://www.ieee-security.org/Cipher/BookReviews/2004/Erickson_by_bruen.html.
- ↑ Stytz, Martin R. (March 2004). "Hacking for Understanding". IEEE. https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=1281235.
- ↑ Henry-Stocker, Sandra (2008-04-02). "Book Review-- Hacking: The Art of Exploitation, 2nd Edition" (in en). https://www.computerworld.com/article/2813444/book-review---hacking--the-art-of-exploitation--2nd-edition.html.
- ↑ Schaefer, Ed. "Hacking: The Art of Exploitation, 2nd Edition » Linux Magazine" (in en-US). http://www.linux-magazine.com/Online/Features/Hacking-The-Art-of-Exploitation-2nd-Edition.
- ↑ "Jon Erickson" (in en). https://www.oreilly.com/pub/au/1648.
Other sources
- Erickson, Jon. Hacking: The Art of Exploitation. No Starch Press, 2003. ISBN:1-59327-007-0
- John Baichtal (March 3, 2008). "GeekDad Review: Hacking: The Art of Exploitation". Wired. http://blog.wired.com/geekdad/2008/03/geekdad-review.html. Retrieved March 27, 2009.
 |