Sigreturn-oriented programming
Sigreturn-oriented programming (SROP) is a computer security exploit technique that allows an attacker to execute code in presence of security measures such as non-executable memory and code signing.[1] It was presented for the first time at the 35th IEEE Symposium on Security and Privacy in 2014 where it won the best student paper award.[2] This technique employs the same basic assumptions behind the return-oriented programming (ROP) technique: an attacker controlling the call stack, for example through a stack buffer overflow, is able to influence the control flow of the program through simple instruction sequences called gadgets. The attack works by pushing a forged sigcontext structure[3] on the call stack, overwriting the original return address with the location of a gadget that allows the attacker to call the sigreturn[4] system call.[5] Often just a single gadget is needed to successfully put this attack into effect. This gadget may reside at a fixed location, making this attack simple and effective, with a setup generally simpler and more portable than the one needed by the plain return-oriented programming technique.[1]
Sigreturn-oriented programming can be considered a weird machine since it allows code execution outside the original specification of the program.[1]
Background
Sigreturn-oriented programming (SROP) is a technique similar to return-oriented programming (ROP), since it employs code reuse to execute code outside the scope of the original control flow. In this sense, the adversary needs to be able to carry out a stack smashing attack, usually through a stack buffer overflow, to overwrite the return address contained inside the call stack.
Stack hopping exploits
If mechanisms such as data execution prevention are employed, it won't be possible for the attacker to just place a shellcode on the stack and cause the machine to execute it by overwriting the return address. With such protections in place, the machine won't execute any code present in memory areas marked as writable and non-executable. Therefore, the attacker will need to reuse code already present in memory.
Most programs do not contain functions that will allow the attacker to directly carry out the desired action (e.g., obtain access to a shell), but the necessary instructions are often scattered around memory.[6]
Return-oriented programming requires these sequences of instructions, called gadgets, to end with a RET instruction. In this way, the attacker can write a sequence of addresses for these gadgets to the stack, and as soon as a RET instruction in one gadget is executed, the control flow will proceed to the next gadget in the list.
Signal handler mechanism
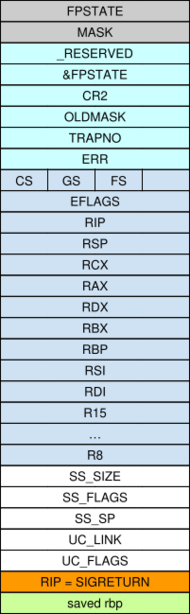
This attack is made possible by how signals are handled in most POSIX-like systems.
Whenever a signal is delivered, the kernel needs to context switch to the installed signal handler. To do so, the kernel saves the current execution context in a frame on the stack.[5][6]
The structure pushed onto the stack is an architecture-specific variant of the sigcontext structure, which holds various data comprising the contents of the registers at the moment of the context switch.
When the execution of the signal handler is completed, the sigreturn() system call is called.
Calling the sigreturn syscall means being able to easily set the contents of registers using a single gadget that can be easily found on most systems.[1]
Differences from ROP
There are several factors that characterize an SROP exploit and distinguish it from a classical return-oriented programming exploit.[7]
First, ROP is dependent on available gadgets, which can be very different in distinct binaries, thus making chains of gadget non-portable. Address space layout randomization (ASLR) makes it hard to use gadgets without an information leakage to get their exact positions in memory.
Although Turing-complete ROP compilers exist,[8] it is usually non-trivial to create a ROP chain.[7]
SROP exploits are usually portable across different binaries with minimal or no effort and allow easily setting the contents of the registers, which could be non-trivial or unfeasible for ROP exploits if the needed gadgets are not present.[6] Moreover, SROP requires a minimal number of gadgets and allows constructing effective shellcodes by chaining system calls. These gadgets are always present in memory, and in some cases are always at fixed locations:[7]
| OS | ASLR | Gadget | Memory Map | Fixed Memory Location |
|---|---|---|---|---|
| Linux i386 | sigreturn | [vdso] | ||
| Linux < 3.11 ARM | sigreturn | [vectors] | 0xffff0000 | |
| Linux < 3.3 x86-64 | syscall&return | [vsyscall] | 0xffffffffff600000 | |
| Linux ≥ 3.3 x86-64 | syscall&return | Libc | ||
| Linux x86-64 | sigreturn | Libc | ||
| FreeBSD 9.2 x86-64 | sigreturn | 0x7ffffffff000 | ||
| Mac OSX x86-64 | sigreturn | Libc | ||
| iOS ARM | sigreturn | Libsystem | ||
| iOS ARM | syscall & return | Libsystem |
Attacks
Linux
An example of the kind of gadget needed for SROP exploits can always be found in the VDSO memory area on x86-Linux systems:
__kernel_sigreturn proc near:
pop eax
mov eax, 77h
int 80h ; LINUX - sys_sigreturn
nop
lea esi, [esi+0]
__kernel_sigreturn endp
On some Linux kernel versions, ASLR can be disabled by setting the limit for the stack size to unlimited,[9] effectively bypassing ASLR and allowing easy access to the gadget present in VDSO.
For Linux kernels prior to version 3.3, it is also possible to find a suitable gadget inside the vsyscall page, which is a mechanism to accelerate the access to certain system calls often used by legacy programs and resides always at a fixed location.
Turing-completeness
It is possible to use gadgets to write into the contents of the stack frames, thereby constructing a self-modifying program. Using this technique, it is possible to devise a simple virtual machine, which can be used as the compilation target for a Turing-complete language.
An example of such an approach can be found in Bosman's paper, which demonstrates the construction of an interpreter for a language similar to the Brainfuck programming language.
The language provides a program counter PC, a memory pointer P, and a temporary register used for 8-bit addition A. This means that also complex backdoors or obfuscated attacks can be devised.[1]
Defenses and mitigations
A number of techniques exists to mitigate SROP attacks, relying on address space layout randomization, canaries and cookies, or shadow stacks.
Address space layout randomization
Address space layout randomization makes it harder to use suitable gadgets by making their locations unpredictable.
Signal cookies
A mitigation for SROP called signal cookies has been proposed. It consists of a way of verifying that the sigcontext structure has not been tampered with by the means of a random cookie XORed with the address of the stack location where it is to be stored. In this way, the sigreturn syscall just needs to verify the cookie's existence at the expected location, effectively mitigating SROP with a minimal impact on performances.[1][10]
Vsyscall emulation
In Linux kernel versions greater than 3.3, the vsyscall interface is emulated, and any attempt to directly execute gadgets in the page will result in an exception.[11][12]
RAP
Grsecurity is a set of patches for the Linux kernel to harden and improve system security.[13] It includes the so-called Return-Address Protection (RAP) to help protect from code reuse attacks.[14]
CET
Starting in 2016, Intel is developing a Control-flow Enforcement Technology (CET) to help mitigate and prevent stack-hopping exploits. CET works by implementing a shadow stack in RAM which will only contain return addresses, protected by the CPU's memory management unit.[15][16]
See also
- Linux kernel interfaces
- Vulnerability (computing)
- Exploit (computer security)
- Buffer overflow
- Address space layout randomization
- Executable space protection
- NX bit
References
- ↑ 1.0 1.1 1.2 1.3 1.4 1.5 "Framing Signals - A Return to Portable Shellcode". 2014 IEEE Symposium on Security and Privacy. 2014. pp. 243–358. doi:10.1109/SP.2014.23. ISBN 978-1-4799-4686-0. http://www.cs.vu.nl/~herbertb/papers/srop_sp14.pdf. Retrieved 2016-06-16.
- ↑ "Award Papers of the 2014 IEEE Symposium on Security and Privacy". IEEE Computer Society's Technical Committee on Security and Privacy. http://www.ieee-security.org/TC/SP2014/oakland2014-best-papers.html.
- ↑ "Linux Cross Reference - sigcontext.h". http://lxr.free-electrons.com/source/arch/x86/include/uapi/asm/sigcontext.h.
- ↑ "SIGRETURN(2) - Linux manual page". http://man7.org/linux/man-pages/man2/sigreturn.2.html.
- ↑ 5.0 5.1 "Playing with signals: An overview on Sigreturn Oriented Programming". https://thisissecurity.net/2015/01/03/playing-with-signals-an-overview-on-sigreturn-oriented-programming/.
- ↑ 6.0 6.1 6.2 "Sigreturn-oriented programming and its mitigation". https://lwn.net/Articles/676803/.
- ↑ 7.0 7.1 7.2 "Framing Signals: a return to portable shellcode". https://tc.gtisc.gatech.edu/bss/2014/r/srop-slides.pdf.
- ↑ "ROPC — Turing complete ROP compiler (part 1)". https://gdtr.wordpress.com/2013/12/13/ropc-turing-complete-rop-compiler-part-1/.
- ↑ "CVE-2016-3672 - Unlimiting the stack not longer disables ASLR". http://hmarco.org/bugs/CVE-2016-3672-Unlimiting-the-stack-not-longer-disables-ASLR.html.
- ↑ "Sigreturn-oriented programming and its mitigation". https://lwn.net/Articles/674861/.
- ↑ "On vsyscalls and the vDSO". https://lwn.net/Articles/446528/.
- ↑ "Hack.lu 2015 - Stackstuff 150: Why and how does vsyscall emulation work". http://toh.necst.it/hack.lu/2015/exploitable/StackStuff/#why-and-how-does-vsyscall-emulation-work.
- ↑ "Linux Kernel Security (SELinux vs AppArmor vs Grsecurity)". http://www.cyberciti.biz/tips/selinux-vs-apparmor-vs-grsecurity.html.
- ↑ "RAP: RIP ROP". https://pax.grsecurity.net/docs/PaXTeam-H2HC15-RAP-RIP-ROP.pdf.
- ↑ "RIP ROP: Intel's cunning plot to kill stack-hopping exploits at CPU level". https://www.theregister.co.uk/2016/06/10/intel_control_flow_enforcement/.
- ↑ "Control-Flow-Enforcement technology preview". https://software.intel.com/sites/default/files/managed/4d/2a/control-flow-enforcement-technology-preview.pdf.
External links
- OHM 2013: Review of “Returning signals for fun and profit
- Playing around with SROP
- Fun with SROP Exploitation
- binjitsu - Sigreturn Oriented Programming
- SigReturn Oriented Programming on x86-64 linux
- Sigreturn ROP exploitation technique (signal's stack frame for the win)
 |
