Software:BestCrypt
From HandWiki
Short description: Commercial disk encryption app available for Windows, Linux, macOS and Android
 | |
 BestCrypt for Windows v9.0 | |
| Developer(s) | Jetico Inc. Oy |
|---|---|
| Initial release | 1995[1] |
| Stable release | 9.08.4
/ May 25, 2023 |
| Operating system |
|
| Size | 5.6–52.3 MB |
| Available in | English, Arabic, Chinese simplified, Czech, Dutch, Persian, French, German, Italian, Latvian, Polish, Russian, Serbian, Spanish, Turkish |
| Type | Disk encryption software |
| License | Trialware |
| Website | www |
BestCrypt, developed by Jetico, is a commercial disk encryption app available for Windows, Linux, macOS and Android.[3]
BestCrypt comes in two editions: BestCrypt Volume Encryption to encrypt entire disk volumes;[4] BestCrypt Container Encryption to encrypt virtual disks stored as computer files.[5]
BestCrypt also provides the complimentary data erasure utility BCWipe.[6]
Cryptographic Algorithms
BestCrypt supports a wide variety of block cipher algorithms including AES, Serpent, Blowfish, Twofish, DES, Triple DES, GOST 28147-89. All ciphers support CBC and LRW modes of operation while AES, Twofish and Serpent also support XTS mode.
Features
- Create and mount a virtual drive encrypted using AES, Blowfish, Twofish, CAST-128[7] and various other encryption methods. BestCrypt v.8 and higher can alternatively mount a subfolder on a NTFS disk instead of a drive. Encrypted virtual disk images are compatible across Windows, Linux and Mac OS X.
- Encrypt a set of files into a single, self-extracting archive.
- Transparently encrypt entire partitions or volumes together with pre-boot authentication for encrypted boot partitions.
- Two-factor authentication.
- Support for size-efficient Dynamic Containers with the Smart Free Space Monitoring technology.[8]
- Hardware accelerated encryption.
- Anti-keylogging facilities to protect container and volume passwords.
- Data erasure utility BCWipe to erase unprotected copies of data to complement encryption.
- Secret sharing and Public Key authentication methods in addition to basic password-based authentication.
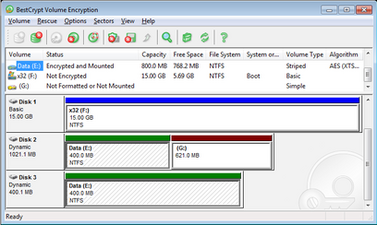
-
BestCrypt Volume Encryption v.3 main window
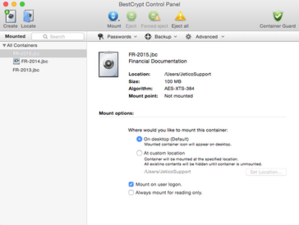
-
BestCrypt for Mac v.1.3 control panel
See also
References
- ↑ "Jetico Inc. Oy Mission". Jetico. http://www.jetico.com/about-jetico/mission-story. Retrieved 2015-01-15.
- ↑ "BestCrypt Explorer on Google play". Jetico. https://play.google.com/store/apps/details?id=com.jetico.bestcrypt&hl=en. Retrieved 2015-01-15.
- ↑ "Data Encryption | Jetico" (in en). https://www.jetico.com/data-encryption.
- ↑ "Encrypt Hard Drives with BestCrypt Volume Encryption | Jetico" (in en). https://www.jetico.com/data-encryption/encrypt-hard-drives-bestcrypt-volume-encryption.
- ↑ "Encrypt Files with BestCrypt Container Encryption | Jetico" (in en). https://www.jetico.com/data-encryption/encrypt-files-bestcrypt-container-encryption.
- ↑ "BestCrypt Container Encryption Features | Jetico" (in en). https://www.jetico.com/data-encryption/encrypt-files-bestcrypt-container-encryption/features.
- ↑ "New Features in BestCrypt Version 8". Jetico. http://www.jetico.com/web_help/bc8/html/03_new_features/01_new_features.htm. Retrieved 2014-04-15.
- ↑ "New Features in BestCrypt Version 9". Jetico Inc. Oy. http://www.jetico.com/web_help/bc9/html/03_new_features/01_new_features.htm. Retrieved 2015-02-04.
Further reading
- Bauer, Mick (2002-06-01). "BestCrypt: Cross-Platform Filesystem Encryption". Linux Journal (Specialized Systems Consultants) 2002 (98): 9. ISSN 1075-3583. http://www.linuxjournal.com/article/5938. Retrieved 2006-11-03.
- "Bestcrypt for Linux documentation". Jetico. 2005-05-17. http://www.jetico.com/linux/bcrypt-help/index.htm. Retrieved 2006-11-03.
External links
 |