Software:MINIX 3
 | |
| Developer | Andrew S. Tanenbaum |
|---|---|
| Written in | C, assembly language |
| OS family | Unix-like |
| Working state | Current |
| Source model | Open source |
| Initial release | 24 October 2005 |
| Marketing target | Embedded systems, education |
| Available in | English |
| Platforms | IA-32, ARM |
| Kernel type | Microkernel |
| Userland | MINIX, NetBSD |
| Default user interface | ash |
| License | custom permissive license |
| Preceded by | Minix 1 and 2 |
| Official website | www |
Minix 3 is a project to create a small, high availability, high functioning Unix-like operating system. It is published under a BSD license and is a successor project to the earlier versions, Minix 1 and 2.
The main goal of the project is for the system to be fault-tolerant by detecting and repairing its own faults on the fly, with no user intervention. The main uses of the system are envisaged to be embedded systems and education.[1]
As of 2017[update], MINIX 3 supports IA-32 and ARM architecture processors.[2] It can also run on emulators or virtual machines, such as Bochs,[3][4] VMware Workstation,[5] Microsoft Virtual PC,[6] Oracle VirtualBox,[7] and QEMU. A port to PowerPC architecture is in development.[8]
The distribution comes on a live CD and can be downloaded as a live USB stick image.[9] The latest release is "minix_R3.4.0rc6-d5e4fc0.iso.bz2" (9 May 2017).[10]
MINIX 3 is believed to be used in the Intel Management Engine (ME) found in Intel's Platform Controller Hub starting with the introduction of ME 11 which is used with Skylake and Kaby Lake processors.[11][12]
Its use in the Intel ME could make it the most widely used OS on x86/AMD64 processors starting as of 2015[update], with more installations than Microsoft Windows, Linux, or macOS.[13]
Goals of the project
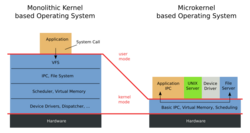
Reflecting on the nature of monolithic kernel based systems, where a driver (which has, according to MINIX creator Tanenbaum, approximately 3–7 times as many bugs as a usual program)[14] can bring down the whole system,[15] MINIX 3 aims to create an operating system that is a "reliable, self-healing, multiserver Unix clone".[16]
To achieve that, the code running in kernel must be minimal, with the file server, process server, and each device driver running as separate user-mode processes. Each driver is carefully monitored by a part of the system named the reincarnation server. If a driver fails to respond to pings from this server, it is shut down and replaced by a fresh copy of the driver.
In a monolithic system, a bug in a driver can easily crash the whole kernel. This is far less likely to occur in MINIX 3.[17]
History
| Version | Release date | Description |
|---|---|---|
| 3.1.0 | 2005-10-24 |
|
| 3.1.2a | 2006-05-29 |
|
| 3.1.3 | 2007-04-13 |
|
| 3.1.3a | 2007-06-08 |
|
| 3.1.4 | 2009-06-09 |
|
| 3.1.5 | 2009-11-05 |
|
| 3.1.6 | 2010-02-08 |
|
| 3.1.7 | 2010-06-16 | |
| 3.1.8 | 2010-10-04 |
|
| 3.2.0 | 2012-02-29 |
|
| 3.2.1 | 2013-02-21 |
|
| 3.3.0 | 2014-09-15 | [20] |
| 3.4.0 rc6 | 2017-05-09 |
|
| ||
MINIX 3 was publicly announced on 24 October 2005 by Andrew Tanenbaum during his keynote speech on top of the Association for Computing Machinery (ACM) Symposium Operating Systems Principles conference. Although it still serves as an example for the new edition of Tanenbaum and Woodhull's textbook, it is comprehensively redesigned to be "usable as a serious system on resource-limited and embedded computers and for applications requiring high reliability."
Reliability policies
One of the main goals of MINIX 3 is reliability. Below, some of the more important principles that enhance its reliability are discussed.
Reduce kernel size
Monolithic operating systems such as Linux and FreeBSD and hybrids like Windows have millions of lines of kernel code. In contrast, MINIX 3 has about 6,000 lines of executable kernel code,[21] which can make problems easier to find in the code.
Cage the bugs
In monolithic kernels, device drivers reside in the kernel. Thus, when a new peripheral is installed, unknown, untrusted code is inserted in the kernel. One bad line of code in a driver can bring down the system.
Instead, in MINIX 3, each device driver is a separate user-mode process. Drivers cannot execute privileged instructions, change the page tables, perform arbitrary input/output (I/O), or write to absolute memory. They must make kernel calls for these services and the kernel checks each call for authority.
Limit drivers' memory access
In monolithic kernels, a driver can write to any word of memory and thus accidentally corrupt user programs.
In MINIX 3, when a user expects data from, for example, the file system, it builds a descriptor telling who has access and at what addresses. It then passes an index to this descriptor to the file system, which may pass it to a driver. The file system or driver then asks the kernel to write via the descriptor, making it impossible for them to write to addresses outside the buffer.
Survive bad pointers
Dereferencing a bad pointer within a driver will crash the driver process, but will have no effect on the system as a whole. The reincarnation server will restart the crashed driver automatically. Users will not notice recovery for some drivers (e.g., disk and network) but for others (e.g., audio and printer), they might. In monolithic kernels, dereferencing a bad pointer in a driver normally leads to a system crash.
Tame infinite loops
If a driver gets into an infinite loop, the scheduler will gradually lower its priority until it becomes idle. Eventually the reincarnation server will see that it is not responding to status requests, so it will kill and restart the looping driver. In a monolithic kernel, a looping driver could hang the system.
Limit damage from buffer overflows
MINIX 3 uses fixed-length messages for internal communication, which eliminates certain buffer overflows and buffer management problems. Also, many exploits work by overrunning a buffer to trick the program into returning from a function call using an overwritten stack return address pointing into attacker controlled memory, usually the overrun buffer. In MINIX 3, this attack is mitigated because instruction and data space are split and only code in (read-only) instruction space can be executed, termed executable space protection. However, attacks which rely on running legitimately executable memory in a malicious way (return-to-libc, return-oriented programming) are not prevented by this mitigation.
Restrict access to kernel functions
Device drivers obtain kernel services (such as copying data to users' address spaces) by making kernel calls. The MINIX 3 kernel has a bit map for each driver specifying which calls it is authorized to make. In monolithic kernels, every driver can call every kernel function, authorized or not.
Restrict access to I/O ports
The kernel also maintains a table telling which I/O ports each driver may access. Thus, a driver can only touch its own I/O ports. In monolithic kernels, a buggy driver can access I/O ports belonging to another device.
Restrict communication with OS components
Not every driver and server needs to communicate with every other driver and server. Accordingly, a per-process bit map determines which destinations each process may send to.
Reincarnate dead or sick drivers
A special process, called the reincarnation server, periodically pings each device driver. If the driver dies or fails to respond correctly to pings, the reincarnation server automatically replaces it with a fresh copy. Detecting and replacing non-functioning drivers is automatic, with no user action needed. This feature does not work for disk drivers at present, but in the next release the system will be able to recover even disk drivers, which will be shadowed in random-access memory (RAM). Driver recovery does not affect running processes.
Integrate interrupts and messages
When an interrupt occurs, it is converted at a low level to a notification sent to the appropriate driver. If the driver is waiting for a message, it gets the interrupt immediately; otherwise it gets the notification the next time it does a RECEIVE to get a message. This scheme eliminates nested interrupts and makes driver programming easier.
Architecture
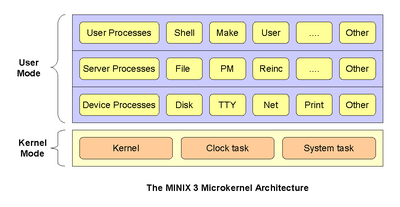
As can be seen, at the bottom level is the microkernel, which is about 4,000 lines of code (mostly in C, plus a small amount of assembly language). It handles interrupts, scheduling, and message passing. It also supports an application programming interface (API) of about 30 kernel calls that authorized servers and drivers can make. User programs cannot make these calls. Instead, they can issue POSIX system calls which send messages to the servers. The kernel calls perform functions such as setting interrupts and copying data between address spaces.
At the next level up, there are the device drivers, each one running as a separate userland process. Each one controls some I/O device, such as a disk or printer. The drivers do not have access to the I/O port space and cannot issue I/O instructions directly. Instead, they must make kernel calls giving a list of I/O ports to write to and the values to be written. While there is a small amount of overhead in doing this (typically 500 ns), this scheme makes it possible for the kernel to check authorization, so that, for example, the audio driver cannot write on the disk.
At the next level there are the servers. This is where nearly all the operating system functionality is located. User processes obtain file service, for example, by sending messages to the file server to open, close, read, and write files. In turn, the file server gets disk I/O performed by sending messages to the disk driver, which controls the disk.
One of the key servers is the reincarnation server. Its job is to poll all the other servers and drivers to check on their health periodically. If a component fails to respond correctly, or exits, or gets into an infinite loop, the reincarnation server (which is the parent process of the drivers and servers) kills the faulty component and replaces it with a fresh copy. In this way the system is automatically made self-healing without interfering with running programs.
Currently the reincarnation server, the process server, and the microkernel are part of the trusted computing base. If any of them fail, the system crashes. Nevertheless, reducing the trusted computing base from 3-5 million lines of code, as in Linux and Windows systems, to about 20,000 lines greatly enhances system reliability.[citation needed]
Differences between MINIX 3 and prior versions
MINIX 1, 1.5, and 2 were developed as tools to help people learn about the design of operating systems.
MINIX 1.0, released in 1987, was 12,000 lines of C and some x86 assembly language. Source code of the kernel, memory manager, and file system of MINIX 1.0 are printed in the book. Tanenbaum originally developed MINIX for compatibility with the IBM PC and IBM PC/AT microcomputers available at the time.
MINIX 1.5, released in 1991, included support for MicroChannel IBM PS/2 systems and was also ported to the Motorola 68000 and SPARC architectures, supporting the Atari ST, Commodore Amiga, Apple Macintosh and Sun Microsystems SPARCstation computer platforms. A version of MINIX running as a user process under SunOS was also available.
MINIX 2.0, released in 1997, was only available for the x86 and Solaris-hosted SPARC architectures. Minix-vmd was created by two Vrije Universiteit researchers, and added virtual memory and support for the X Window System.
MINIX 3 does the same, and provides a modern operating system with many newer tools and many Unix applications.[22] Prof. Tanenbaum once said:
| “ | Please be aware that MINIX 3 is not your grandfather's MINIX ... MINIX 1 was written as an educational tool ... MINIX 3 is that plus a start at building a highly reliable, self-healing, bloat-free operating system ... MINIX 1 and MINIX 3 are related in the same way as Windows 3.1 and Windows XP are: same first name.[16] | ” |
Many improvements have also been made in the structure of the kernel since the MINIX 2 release, making the system more reliable.[23] MINIX version 3.1.5 was released 5 Nov 2009. It contains X11, Emacs, vi, cc, GCC, Perl, Python, Almquist shell, Bash, Z shell, FTP client, SSH client, Telnet client, Pine, and over 400 other common Unix utility programs. With the addition of X11, this version marks the transition away from a text-only system. Another feature of this version, which will be improved in future ones, is the ability of the system to withstand device driver crashes, and in many cases having them automatically replaced without affecting running processes. In this way, MINIX is self-healing and can be used in applications demanding high reliability.
MINIX 3.2.0 was released in February 2012. This version has many new features, including the Clang compiler, experimental symmetric multiprocessing support, procfs and ext2fs filesystem support, and GNU Debugger (GDB). Several parts of NetBSD are also integrated in the release, including the bootloader, libc and various utilities and other libraries.[24]
MINIX 3.3.0 was released in September 2014. This release is the first version to support the ARM architecture in addition to x86. It also supports a NetBSD userland, with thousands of NetBSD packages running right out of the box.
Mascot

Rocky Raccoon is the mascot of MINIX 3.[25]
MINIXCon
MINIXCon is a conference on sharing talks, efforts and researches related to MINIX.
MINIXCon2017 was cancelled due lack of talks submitted.[26][27]
See also
- Comparison of operating system kernels
- MINIX file system
- List of computing mascots
References
- ↑ corbet (2005-10-24). "Minix 3 hits the net". Lwn.net. https://lwn.net/Articles/156828/.
- ↑ "minix3.org". minix3.org. http://www.minix3.org.
- ↑ "Getting Started with Minix on Bochs on Mac OS". Woodhull.com. http://www.woodhull.com/newfaq/faq/bochstart.html.
- ↑ "OSNews.com". OSNews.com. http://www.osnews.com/story.php?news_id=7303.
- ↑ "Minix under VMWare Installation How-To". Patrick.wagstrom.net. http://patrick.wagstrom.net/projects/academic/cs551/minix.html.
- ↑ "Minix on Virtual PC: first look". Woodhull.com. http://www.woodhull.com/newfaq/faq/pre-vpc.html.
- ↑ "Minix 3 on Virtual box". inopinion.org. http://www.inopinion.org/howto/install-minix-3-on-virtual-box/.
- ↑ Alting, Ingmar. "A port of the MINIX OS to the PowerPC platform". http://www.minix3.org/doc/alting_thesis.pdf.
- ↑ "Minix3". Minix3. http://www.minix3.org/download.
- ↑ http://download.minix3.org/iso/snapshot/
- ↑ "Intel ME: The Way of Static Analysis". http://blog.ptsecurity.com/2017/04/intel-me-way-of-static-analysis.html.
- ↑ Corna, Nicola (2017-08-28). "me_cleaner: Tool for partial deblobbing of Intel ME/TXE firmware images". https://github.com/corna/me_cleaner.
- ↑ http://www.cs.vu.nl/~ast/intel/
- ↑ Tanenbaum, Andy (2006-09-25). "Introduction to MINIX 3". OSnew. OSnews. http://osnews.com/story.php/15960/Introduction-to-MINIX-3. "From Rebirth section: "Various studies have shown that software broadly contains something like 6-16 bugs per 1000 lines of code and that device drivers have 3-7 times as many bugs as the rest of the operating system. When combined with the fact that 70% of a typical operating system consists of device drivers, it is clear that device drivers are a big source of trouble. For Windows XP, 85% of the crashes are due to bugs in device drivers. Obviously, to make OSes reliable, something has to be done to deal with buggy device drivers. Building a reliable system despite the inevitable bugs in device drivers was the original driving force behind MINIX 3.""
- ↑ "CSAIL Event Calendar". Csail.mit.edu. http://www.csail.mit.edu/events/eventcalendar/calendar.php?show=event&id=1128.
- ↑ 16.0 16.1 "Tanenbaum-Torvalds debate, Part II". Cs.vu.nl. 2006-05-12. http://www.cs.vu.nl/~ast/reliable-os/.
- ↑ http://www.MINIX3.org/reliability.html
- ↑ "MinixReleases – Minix Wiki". Wiki.minix3.org. https://wiki.minix3.org/doku.php?id=releases:start.
- ↑ Swift, Björn Patrick. "Individual Programming Assignment User Mode Scheduling in MINIX 3" (PDF). Minix3.org. http://www.minix3.org/docs/scheduling/report.pdf.
- ↑ MINIX Release 3.3.0
- ↑ "The MINIX 3 Operating System". minix3.org. http://www.minix3.org/.
- ↑ "FAQ – Minix Wiki". Minix3.org. 2013-11-09. http://www.MINIX3.org/doc/faq.html.
- ↑ http://www.minix3.org/improvements.html
- ↑ "MINIX Releases". wiki.minix3.org. Archived from the original on 18 June 2012. https://www.webcitation.org/68WUo9Bot?url=http://wiki.minix3.org/en/MinixReleases.
- ↑ "mascot [Wiki"] (in en). http://wiki.minix3.org/doku.php?id=mascot.
- ↑ "Minix3". http://www.minix3.org/.
- ↑ "Minix3". http://www.minix3.org/news/index.html.
Further reading
- Tanenbaum, Andrew S; Woodhull, Albert S. (14 January 2006). Operating Systems: Design and Implementation (3rd ed.). Prentice Hall. ISBN 0-13-142938-8. http://www.pearsonhighered.com/educator/academic/product/0,,0131429388,00%2Ben-USS_01DBC.html.
- Building a dependable operating system: fault tolerance in MINIX 3 by Jorrit N. Herder (PDF)
- Reorganizing Unix for Reliability by Jorrit N. Herder, Herbert Bos, Ben Gras, Philip Homburg, and Andrew S. Tanenbaum (PDF)
- Modular system programming in MINIX 3 by Jorrit N. Herder, Herbert Bos, Ben Gras, Philip Homburg, and Andrew S Tanenbaum (PDF)
- J. N. Herder et al., Modular System Programming in MINIX 3, ;Login, April 2006 (PDF)
- Pablo A Pessolani. MINIX4RT: A Real-Time Operating System Based on MINIX
- Building Performance Measurement Tools for the MINIX 3 Operating System, by Rogier Meurs (PDF)
- Design and implementation of the MINIX virtual file system (PDF)
- Reference manual for MINIX 3 Kernel API (PDF)
- Towards a true microkernel operating system (PDF)
- Construction of a Highly Dependable Operating System (PDF)
- Minix 3 and the microkernel experience: Smart Kernel by Rüdiger Weis (PDF)
- Safe and Automatic Live Update by Cristiano Giuffrida (PDF)
External links
- minix3.ru (in Russian)
- comp.os.minix – official forum (since 1987)
- Description of Minix 3 by Andy Tanenbaum
- MINIX: what is it, and why is it still relevant? An interview with Andy Tanenbaum
- Minix Network Service Documentation
- Can We Make Operating Systems Reliable and Secure?
- A reimplementation of NetBSD based on a microkernel
- MINIX 3 on ARM by Kees Jongenburger
- Lessons Learned from 30 Years of MINIX By Andrew S. Tanenbaum
